Pass CompTIA Security+ SY0-701 in Just 3 Days – Stress-Free!
Get your Security+ SY0-701 certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
A security officer is implementing a security awareness program and has placed security-themed posters around the building and assigned online user training. Which of the following will the security officer most likely implement?
- A. Password policy
- B. Access badges
- C. Phishing campaign
- D. Risk assessment
A malicious update was distributed to a common software platform and disabled services at many organizations. Which of the following best describes this type of vulnerability?
- A. DDoS attack
- B. Rogue employee
- C. Insider threat
- D. Supply chain
A company web server is initiating outbound traffic to a low-reputation, public IP on non-standard pat. The web server is used to present an unauthenticated page to clients who upload images the company. An analyst notices a suspicious process running on the server hat was not created by the company development team. Which of the following is the most likely explanation for his security incident?
- A. A web shell has been deployed to the server through the page.
- B. A vulnerability has been exploited to deploy a worm to the server.
- C. Malicious insiders are using the server to mine cryptocurrency.
- D. Attackers have deployed a rootkit Trojan to the server over an exposed RDP port.
An organization requests a third-party full-spectrum analysis of its supply chain. Which of the following would the analysis team use to meet this requirement?
- A. Vulnerability scanner
- B. Penetration test
- C. SCAP
- D. Illumination tool
A systems administrator deployed a monitoring solution that does not require installation on the endpoints that the solution is monitoring. Which of the following is described in this scenario?
- A. Agentless solution
- B. Client-based soon
- C. Open port
- D. File-based solution
A security analyst is reviewing the source code of an application in order to identify misconfigurations and vulnerabilities. Which of the following kinds of analysis best describes this review?
- A. Dynamic
- B. Static
- C. Gap
- D. Impact
Which of the following agreement types is used to limit external discussions?
- A. BPA
- B. NDA
- C. SLA
- D. MSA
A security analyst is evaluating a SaaS application that the human resources department would like to implement. The analyst requests a SOC 2 report from the SaaS vendor. Which of the following processes is the analyst most likely conducting?
- A. Internal audit
- B. Penetration testing
- C. Attestation
- D. Due diligence
Which of the following is used to conceal credit card information in a database log file?
- A. Tokenization
- B. Masking
- C. Hashing
- D. Obfuscation
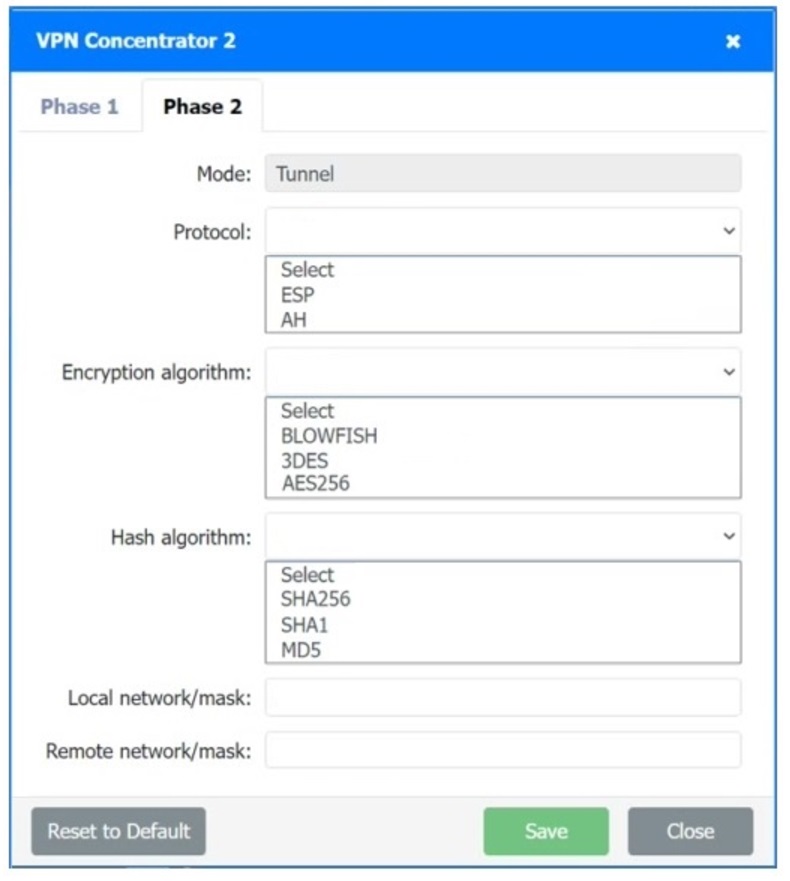
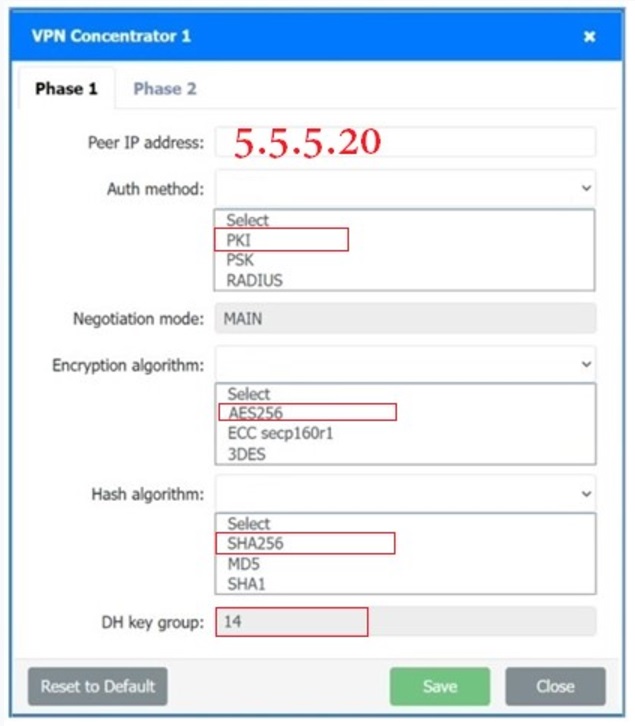
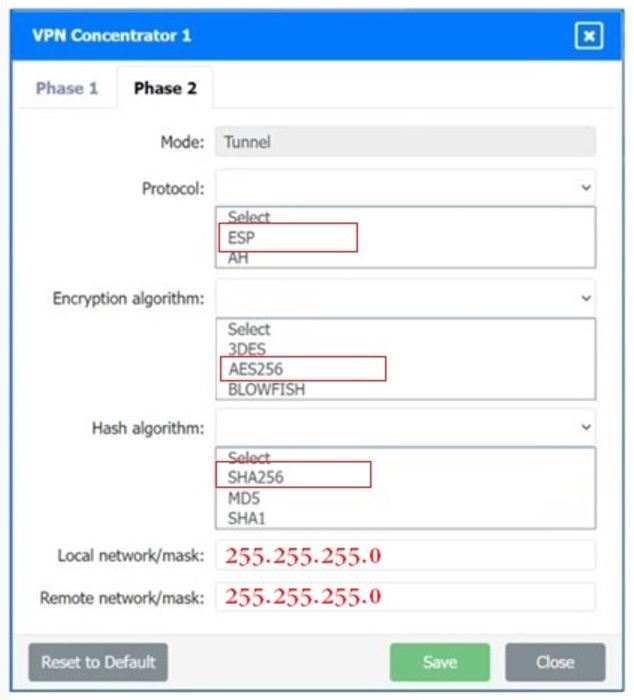
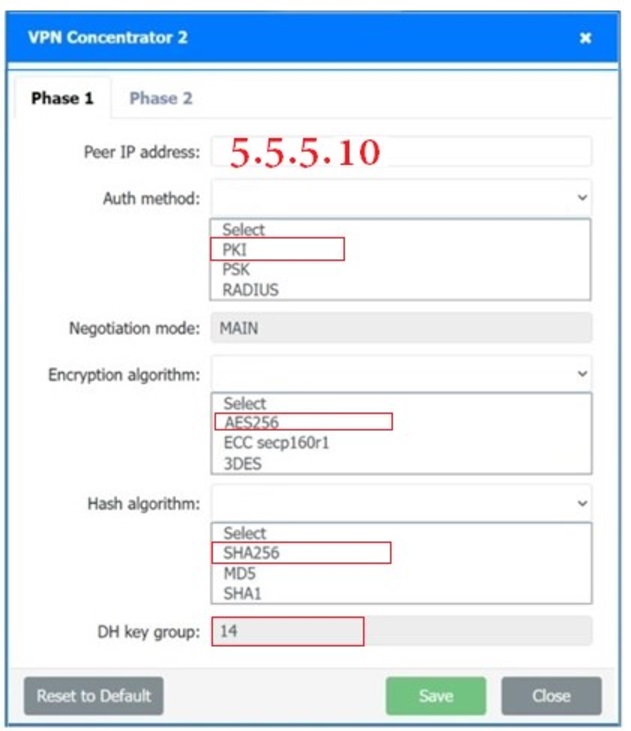
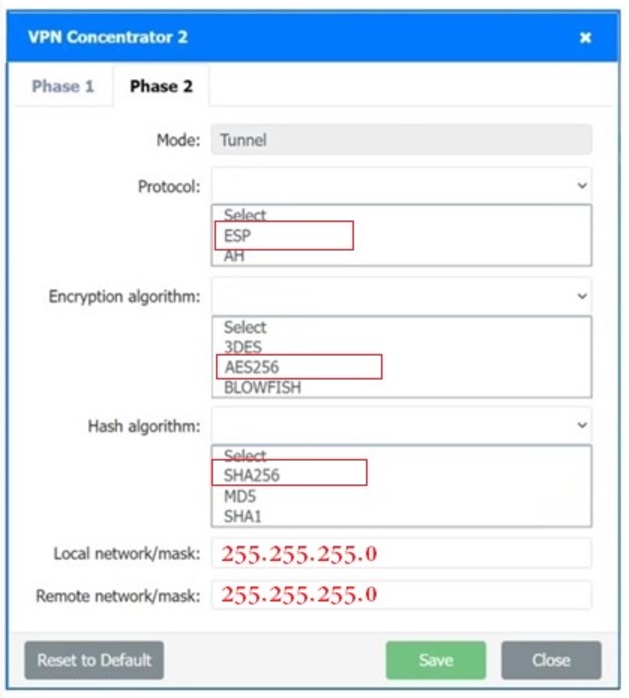
SIMULATION
–
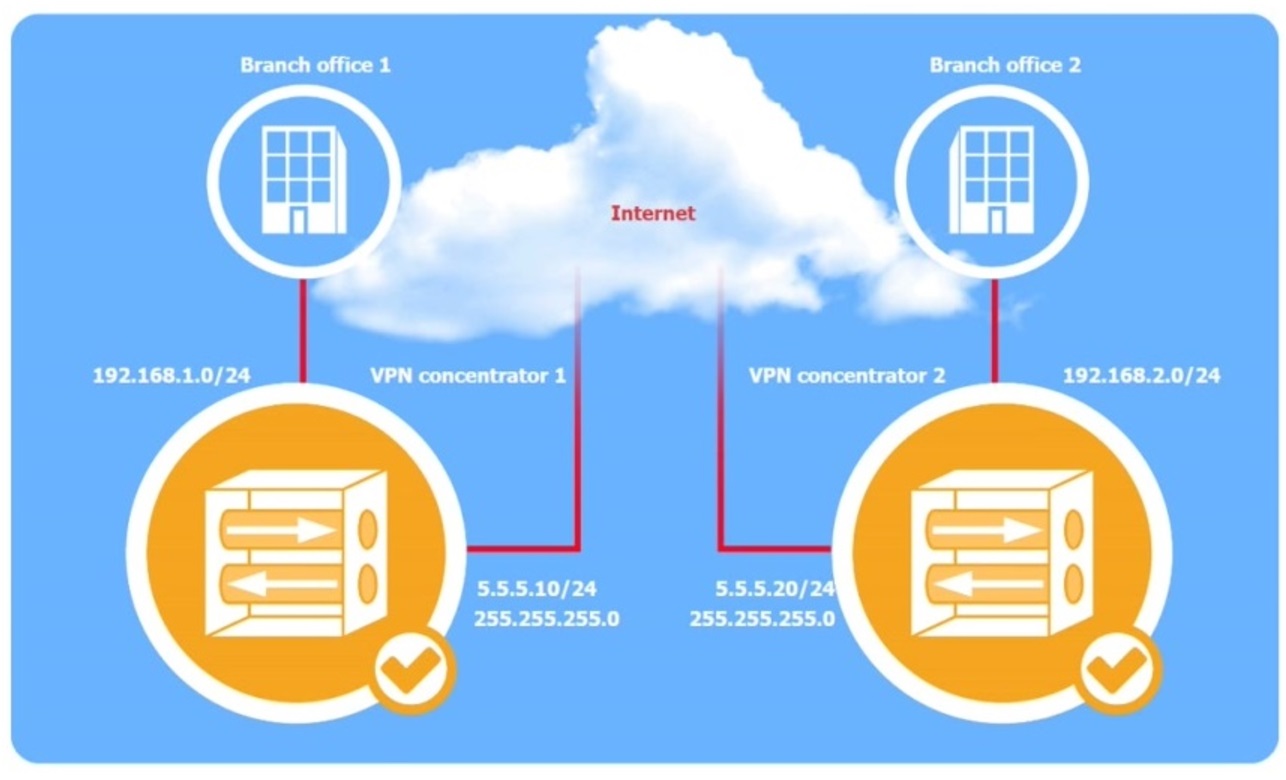
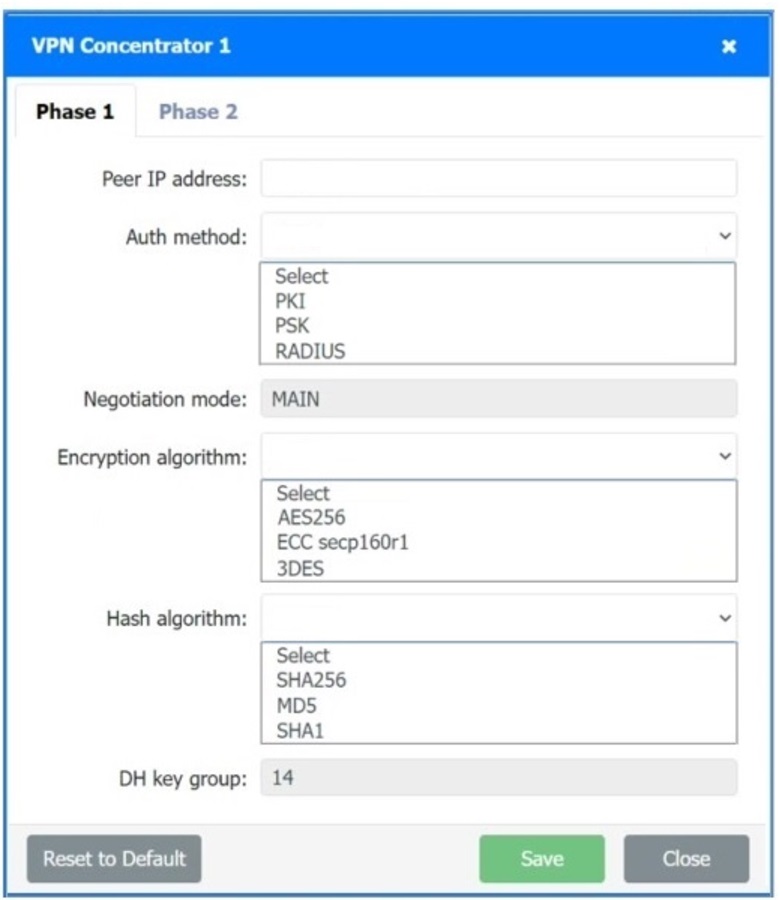
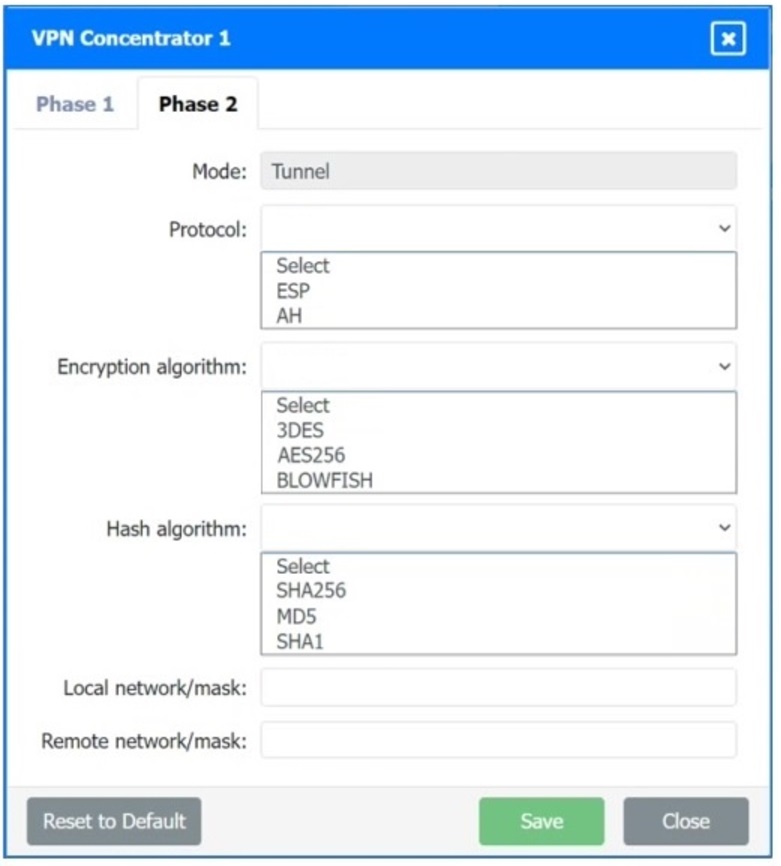
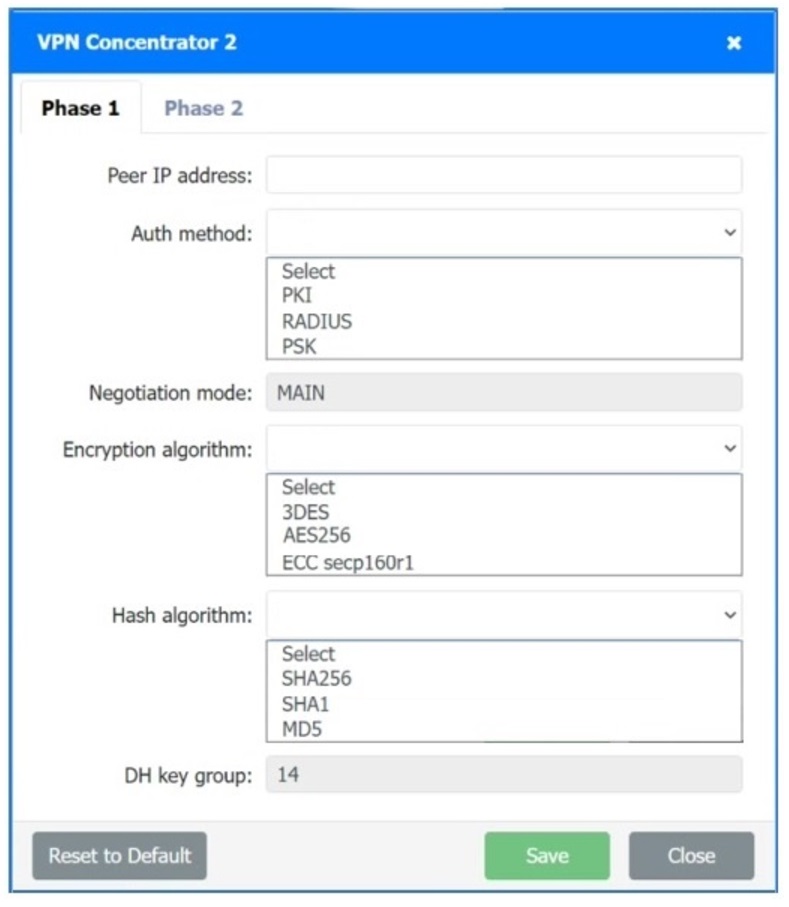
A systems administrator is configuring a site-to-site VPN between two branch offices. Some of the settings have already been configured correctly. The systems administrator has been provided the following requirements as part of completing the configuration:
• Most secure algorithms should be selected
• All traffic should be encrypted over the VPN
• A secret password will be used to authenticate the two VPN concentrators
INSTRUCTIONS
–
Click on the two VPN Concentrators to configure the appropriate settings.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.