
Pass CompTIA Security+ SY0-701 in Just 3 Days – Stress-Free!
Get your Security+ SY0-701 certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
An organization recently started hosting a new service that customers access through a web portal. A security engineer needs to add to the existing security devices a new solution to protect this new service. Which of the following is the engineer most likely to deploy?
- A. Layer 4 firewall
- B. NGFW
- C. WAF
- D. UTM
Which of the following topics would most likely be included within an organization’s SDLC?
- A. Service-level agreements
- B. Information security policy
- C. Penetration testing methodology
- D. Branch protection requirements
Which of the following control types is AUP an example of?
- A. Physical
- B. Managerial
- C. Technical
- D. Operational
An organization is adopting cloud services at a rapid pace and now has multiple SaaS applications in use. Each application has a separate log-in, so the security team wants to reduce the number of credentials each employee must maintain. Which of the following is the first step the security team should take?
- A. Enable SAML.
- B. Create OAuth tokens.
- C. Use password vaulting.
- D. Select an IdP.
A company’s online shopping website became unusable shortly after midnight on January 30, 2023. When a security analyst reviewed the database server, the analyst noticed the following code used for backing up data:
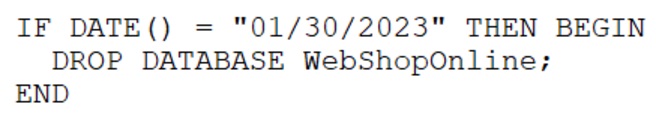
Which of the following should the analyst do next?
- A. Check for recently terminated DBAs.
- B. Review WAF logs for evidence of command injection.
- C. Scan the database server for malware.
- D. Search the web server for ransomware notes.
Which of the following would be the best way to test resiliency in the event of a primary power failure?
- A. Parallel processing
- B. Tabletop exercise
- C. Simulation testing
- D. Production failover
Which of the following would be the most appropriate way to protect data in transit?
- A. SHA-256
- B. SSL3.0
- C. TLS 1.3
- D. AES-256
Which of the following is a common, passive reconnaissance technique employed by penetration testers in the early phases of an engagement?
- A. Open-source intelligence
- B. Port scanning
- C. Pivoting
- D. Exploit validation
Which of the following threat actors is the most likely to seek financial gain through the use of ransomware attacks?
- A. Organized crime
- B. Insider threat
- C. Nation-state
- D. Hacktivists
Which of the following would a systems administrator follow when upgrading the firmware of an organization’s router?
- A. Software development life cycle
- B. Risk tolerance
- C. Certificate signing request
- D. Maintenance window
