
Pass CompTIA Security+ SY0-701 in Just 3 Days – Stress-Free!
Get your Security+ SY0-701 certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
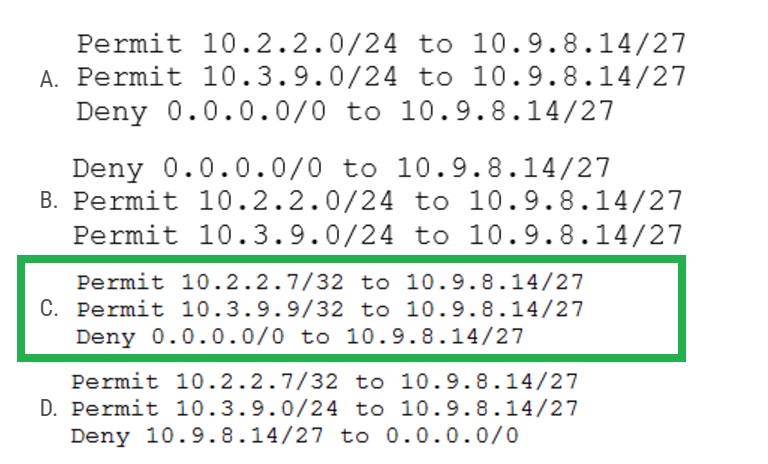
The security team has been asked to only enable host A (10.2.2.7) and host B (10.3.9.9) to the new isolated network segment (10.9.8.14) that provides access to legacy devices.
Access from all other hosts should be blocked. Which of the following entries would need to be added on the firewall?
A systems administrator needs to ensure the secure communication of sensitive data within the organization’s private cloud. Which of the following is the best choice for the administrator to implement?
- A. IPSec
- B. SHA-1
- C. RSA
- D. TGT
Which of the following should an internal auditor check for first when conducting an audit of the organization’s risk management program?
- A. Policies and procedures
- B. Asset management
- C. Vulnerability assessment
- D. Business impact analysis
Which of the following activities are associated with vulnerability management? (Choose two.)
- A. Reporting
- B. Prioritization
- C. Exploiting
- D. Correlation
- E. Containment
- F. Tabletop exercise
An administrator wants to perform a risk assessment without using proprietary company information. Which of the following methods should the administrator use to gather information?
- A. Network scanning
- B. Penetration testing
- C. Open-source intelligence
- D. Configuration auditing
A systems administrator is concerned about vulnerabilities within cloud computing instances. Which of the following is most important for the administrator to consider when architecting a cloud computing environment?
- A. SQL injection
- B. TOC/TOU
- C. VM escape
- D. Tokenization
- E. Password spraying
A database administrator is updating the company’s SQL database, which stores credit card information for pending purchases. Which of the following is the best method to secure the data against a potential breach?
- A. Hashing
- B. Obfuscation
- C. Tokenization
- D. Masking
Which of the following is a benefit of vendor diversity?
- A. Patch availability
- B. Zero-day resiliency
- C. Secure configuration guide applicability
- D. Load balancing
An employee used a company’s billing system to issue fraudulent checks. The administrator is looking for evidence of other occurrences of this activity. Which of the following should the administrator examine?
- A. Application logs
- B. Vulnerability scanner logs
- C. IDS/IPS logs
- D. Firewall logs
