
Pass CompTIA Security+ SY0-701 in Just 3 Days – Stress-Free!
Get your Security+ SY0-701 certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
A security officer is implementing a security awareness program and is placing security-themed posters around the building and is assigning online user training. Which of the following would the security officer most likely implement?
- A. Password policy
- B. Access badges
- C. Phishing campaign
- D. Risk assessment
A security consultant is working with a client that wants to physically isolate its secure systems. Which of the following best describes this architecture?
- A. SDN
- B. Air gapped
- C. Containerized
- D. Highly available
A company is in the process of migrating to cloud-based services. The company’s IT department has limited resources for migration and ongoing support. Which of the following best meets the company’s needs?
- A. IPS
- B. WAF
- C. SASE
- D. IAM
- An employee clicks a malicious link in an email that appears to be from the company’s Chief Executive Officer. The employee’s computer is infected with ransomware that encrypts the company’s files. Which of the following is the most effective way for the company to prevent similar incidents in the future?
- A. Security awareness training
- B. Database encryption
- C. Segmentation
- D. Reporting suspicious emails
Which of the following types of vulnerabilities is primarily caused by improper use and management of cryptographic certificates?
- A. Misconfiguration
- B. Resource reuse
- C. Insecure key storage
- D. Weak cipher suites
Which of the following best describe the benefits of a microservices architecture when compared to a monolithic architecture? (Choose two.)
- A. Easier debugging of the system
- B. Reduced cost of ownership of the system
- C. Improved scalability of the system
- D. Increased compartmentalization of the system
- E. Stronger authentication of the system
- F. Reduced complexity of the system
A user’s workstation becomes unresponsive and displays a ransom note demanding payment to decrypt files. Before the attack, the user opened a resume they received in a message, browsed the company’s website, and installed OS updates. Which of the following is the most likely vector of this attack?
- A. Spear-phishing attachment
- B. Watering hole
- C. Infected website
- D. Typosquatting
A penetration tester finds an unused Ethernet port during an on-site penetration test. Upon plugging a device into the unused port, the penetration tester notices that the machine is assigned an IP address, allowing the tester to enumerate the local network. Which of the following should an administrator implement in order to prevent this situation from happening in the future?
- A. Port security
- B. Transport Layer Security
- C. Proxy server
- D. Security zones
Which of the following should be used to ensure an attacker is unable to read the contents of a mobile device’s drive if the device is lost?
- A. TPM
- B. ECC
- C. FDE
- D. HSM
A security administrator documented the following records during an assessment of network services:
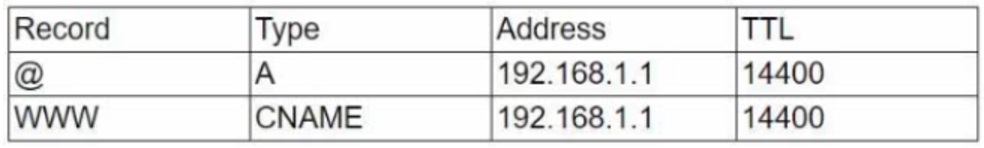
Two weeks later, the administrator performed a log review and noticed the records were changed as follows:
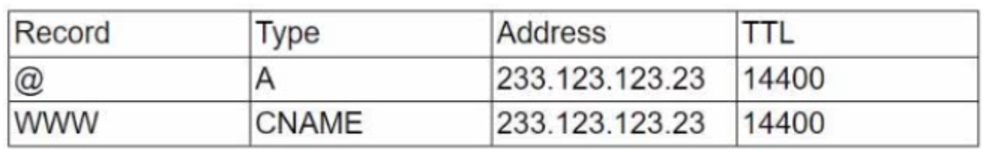
When consulting the service owner, the administrator validated that the new address was not part of the company network. Which of the following was the company most likely experiencing?
- A. DDoS attack
- B. DNS poisoning
- C. Ransomware compromise
- D. Spyware infection
