
Pass CompTIA Security+ SY0-701 in Just 3 Days – Stress-Free!
Get your Security+ SY0-701 certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
A systems administrator is reviewing the VPN logs and notices that during non-working hours a user is accessing the company file server and information is being transferred to a suspicious IP address. Which of the following threats is most likely occurring?
- A. Typosquatting
- B. Root or trust
- C. Data exfiltration
- D. Blackmail
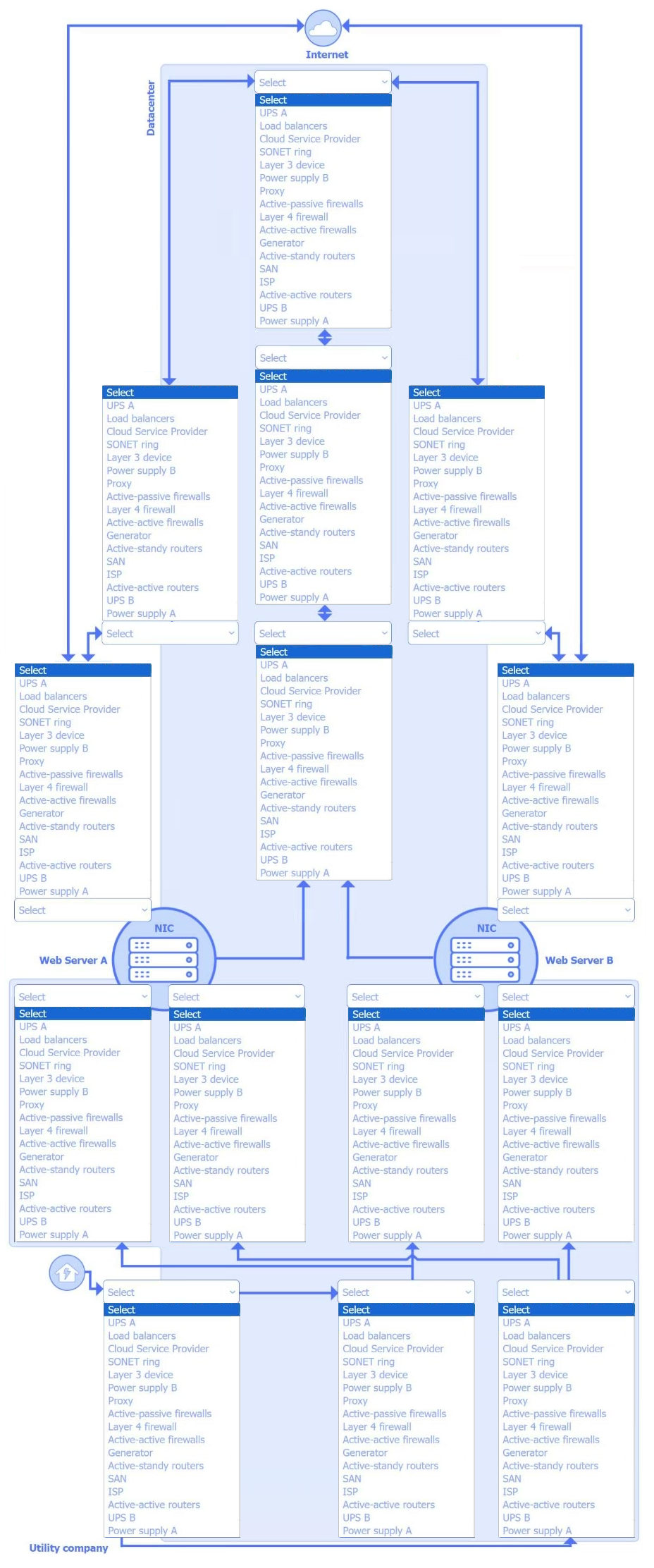
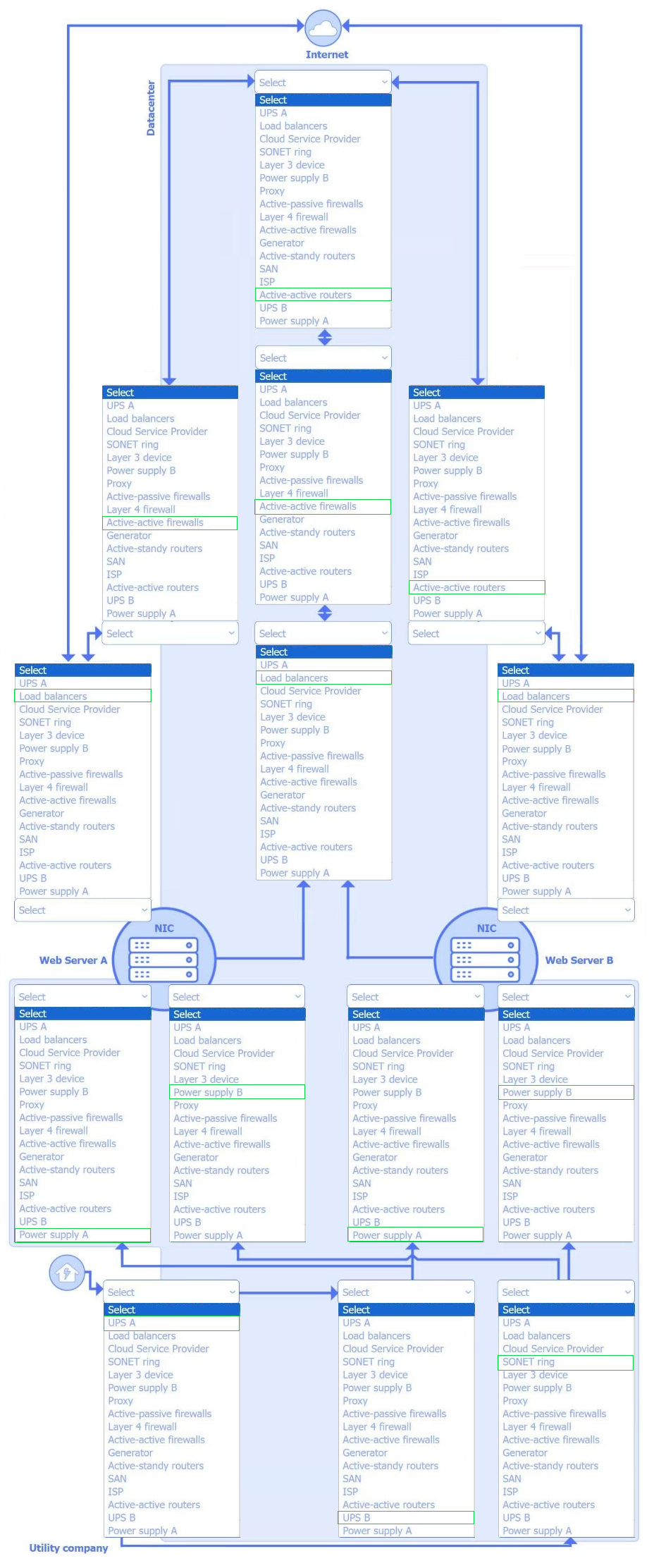
HOTSPOT
–
A security architect is tasked with designing a highly resilient, business-critical application. The application SLA is 99.999%.
INSTRUCTIONS
–
Select the network, power, and server components for the appropriate locations to achieve application resiliency.
A component should be selected for each location, and components may be selected more than once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A company discovers suspicious transactions that were entered into the company’s database and attached to a user account that was created as a trap for malicious activity. Which of the following is the user account an example of?
A. Honeytoken
B. Honeynet
C. Honeypot
D. Honeyfile
A network engineer is increasing the overall security of network devices and needs to harden the devices. Which of the following will best accomplish this task?
- A. Configuring centralized logging
- B. Generating local administrator accounts
- C. Replacing Telnet with SSH
- D. Enabling HTTP administration
A company’s accounting department receives an urgent payment message from the company’s bank domain with instructions to wire transfer funds. The sender requests that the transfer be completed as soon as possible. Which of the following attacks is described?
- A. Business email compromise
- B. Vishing
- C. Spear phishing
- D. Impersonation
A company filed a complaint with its IT service provider after the company discovered the service provider’s external audit team had access to some of the company’s confidential information. Which of the following is the most likely reason the company filed the complaint?
- A. The MOU had basic clauses from a template.
- B. A SOW had not been agreed to by the client.
- C. A WO had not been mutually approved.
- D. A required NDA had not been signed.
Which of the following aspects of the data management life cycle is most directly impacted by local and international regulations?
- A. Destruction
- B. Certification
- C. Retention
- D. Sanitization
An analyst is reviewing job postings to ensure sensitive company information is not being shared with the general public. Which of the following is the analyst most likely looking for?
- A. Office addresses
- B. Software versions
- C. List of board members
- D. Government identification numbers
An engineer has ensured that the switches are using the latest OS, the servers have the latest patches, and the endpoints’ definitions are up to date. Which of the following will these actions most effectively prevent?
- A. Zero-day attacks
- B. Insider threats
- C. End-of-life support
- D. Known exploits
Which of the following is most likely a security concern when installing and using low-cost IoT devices in infrastructure environments?
- A. Country of origin
- B. Device responsiveness
- C. Ease of deployment
- D. Storage of data
