
Pass CompTIA Security+ SY0-701 in Just 3 Days – Stress-Free!
Get your Security+ SY0-701 certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
Question 71
A security analyst reviews domain activity logs and notices the following:

Which of the following is the best explanation for what the security analyst has discovered?
- A. The user jsmith’s account has been locked out.
- B. A keylogger is installed on jsmith’s workstation.
- C. An attacker is attempting to brute force jsmith’s account.
- D. Ransomware has been deployed in the domain.
A company is concerned about weather events causing damage to the server room and downtime. Which of the following should the company consider?
- A. Clustering servers
- B. Geographic dispersion
- C. Load balancers
- D. Off-site backups
Which of the following is a primary security concern for a company setting up a BYOD program?
- A. End of life
- B. Buffer overflow
- C. VM escape
- D. Jailbreaking
A company decided to reduce the cost of its annual cyber insurance policy by removing the coverage for ransomware attacks.
Which of the following analysis elements did the company most likely use in making this decision?
- A. MTTR
- B. RTO
- C. ARO
- D. MTBF
Which of the following is the most likely to be included as an element of communication in a security awareness program?
- A. Reporting phishing attempts or other suspicious activities
- B. Detecting insider threats using anomalous behavior recognition
- C. Verifying information when modifying wire transfer data
- D. Performing social engineering as part of third-party penetration testing
HOTSPOT –
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS –
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button
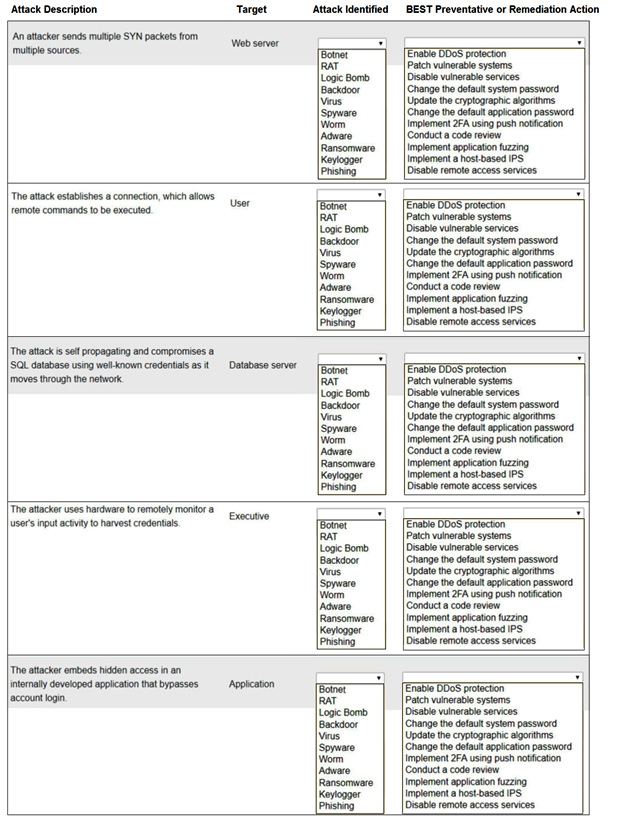
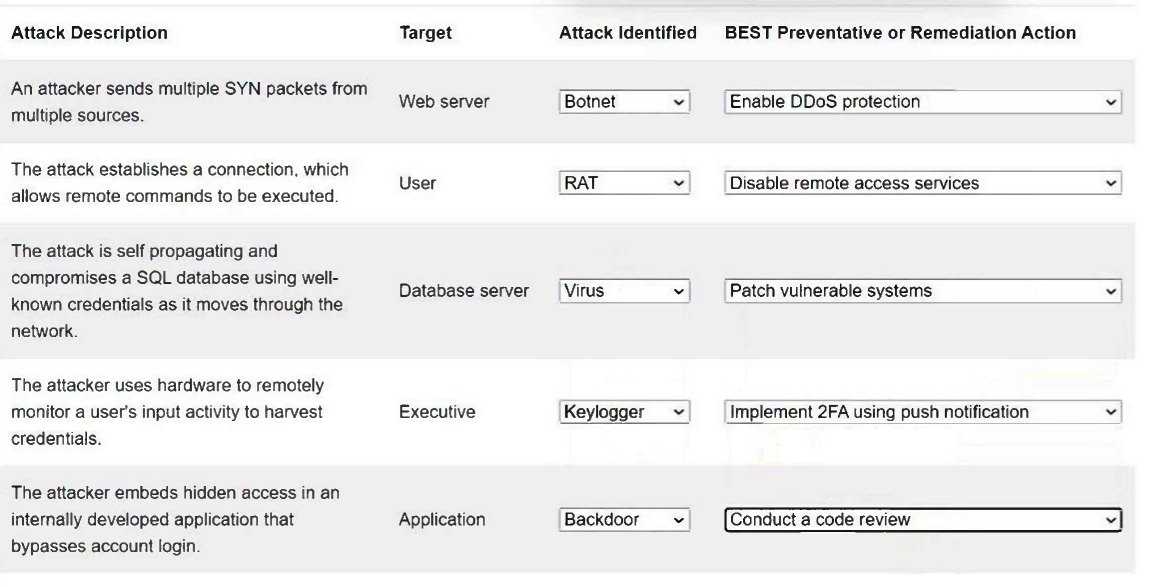
HOTSPOT –
You are a security administrator investigating a potential infection on a network.
INSTRUCTIONS –
Click on each host and firewall. Review all logs to determine which host originated the infection and then identify if each remaining host is clean or infected.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
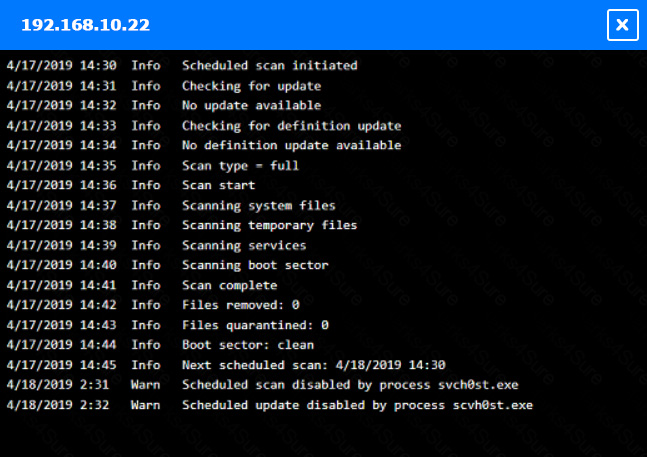
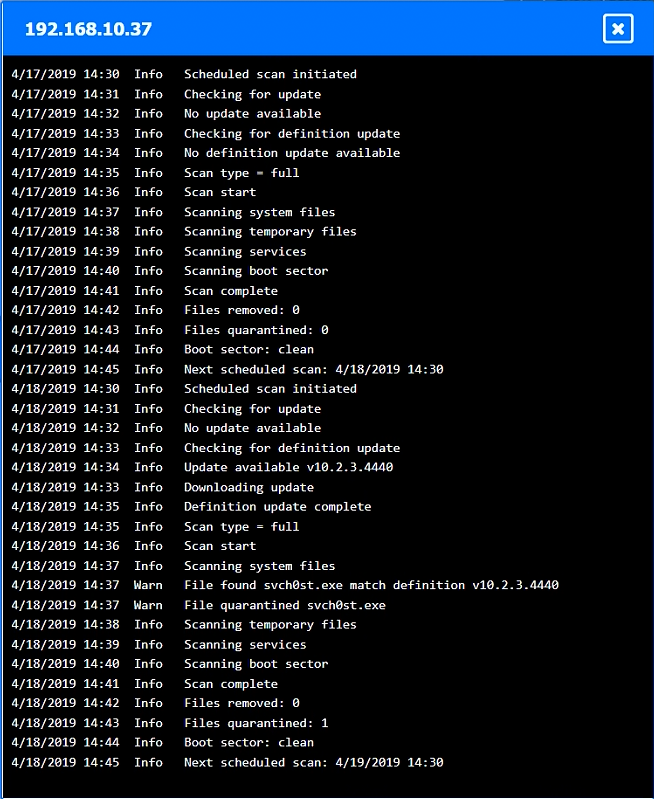
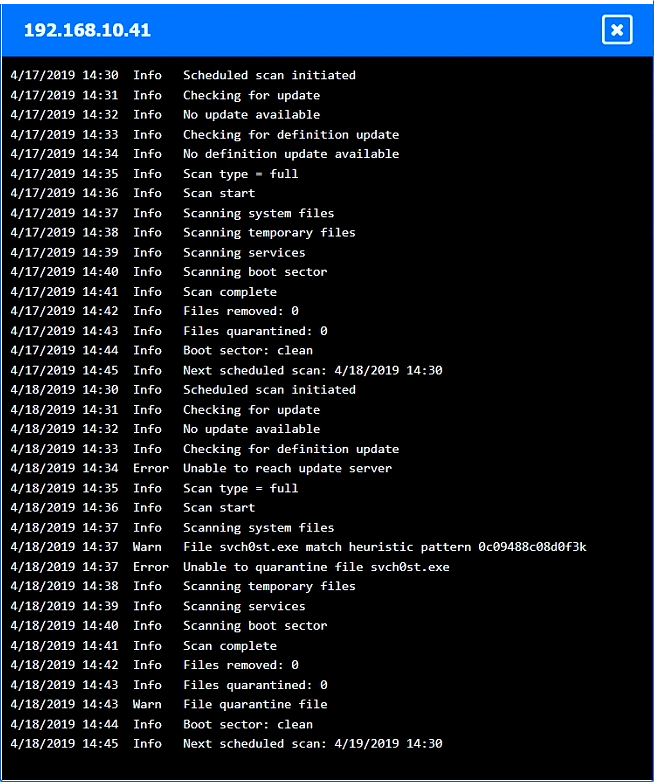
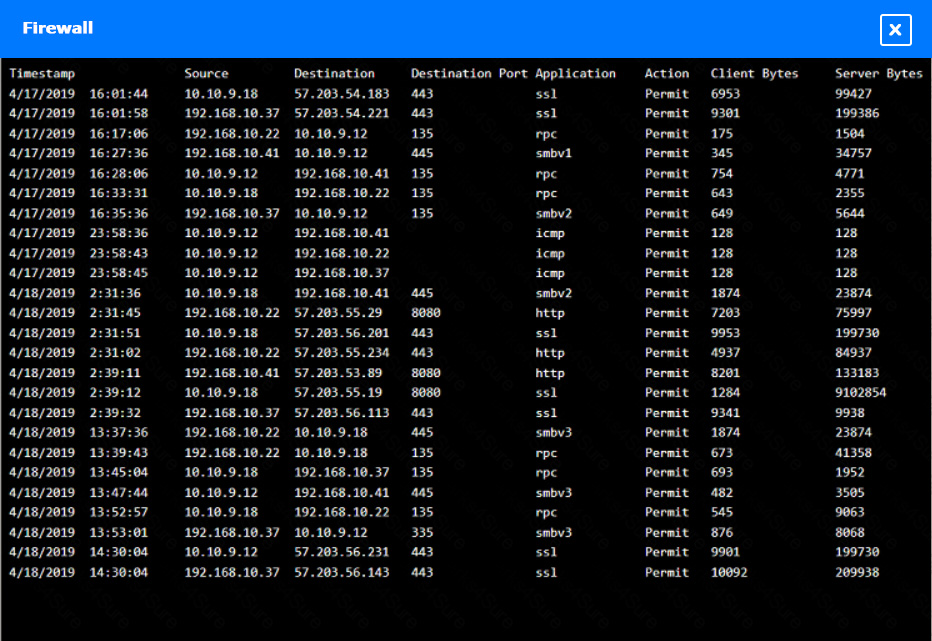
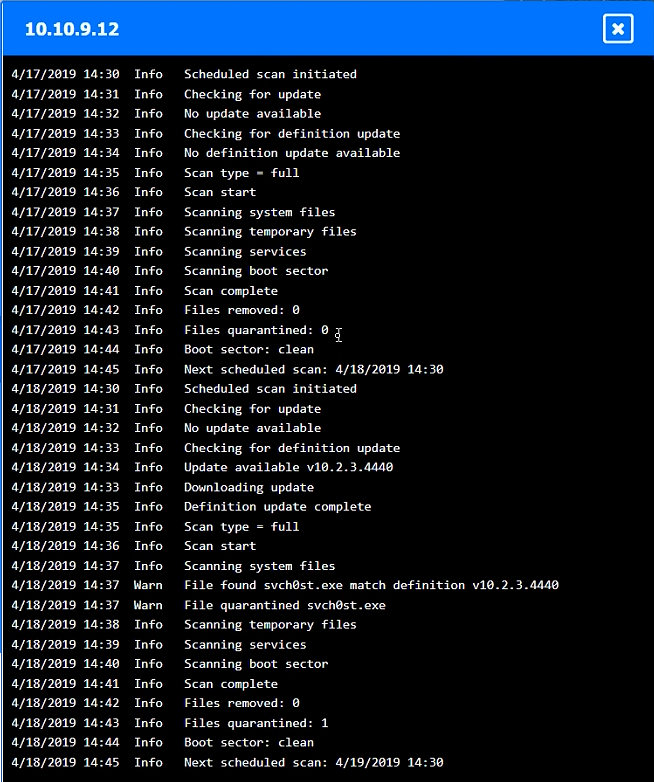
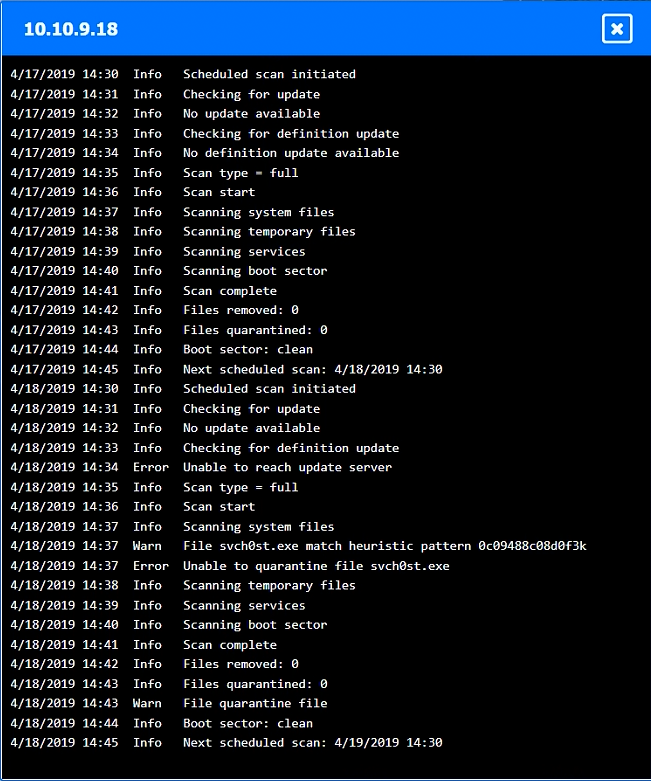
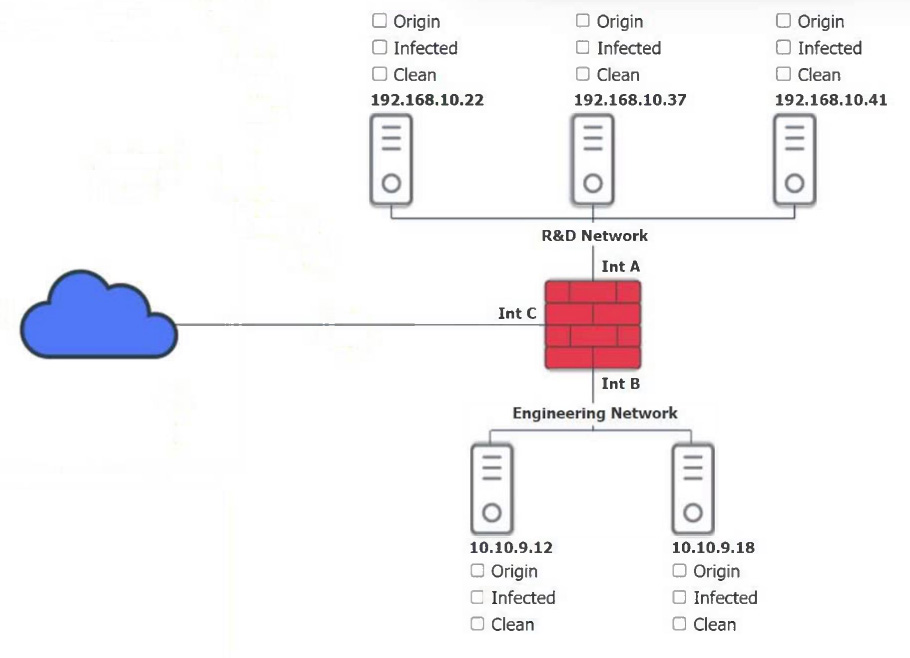
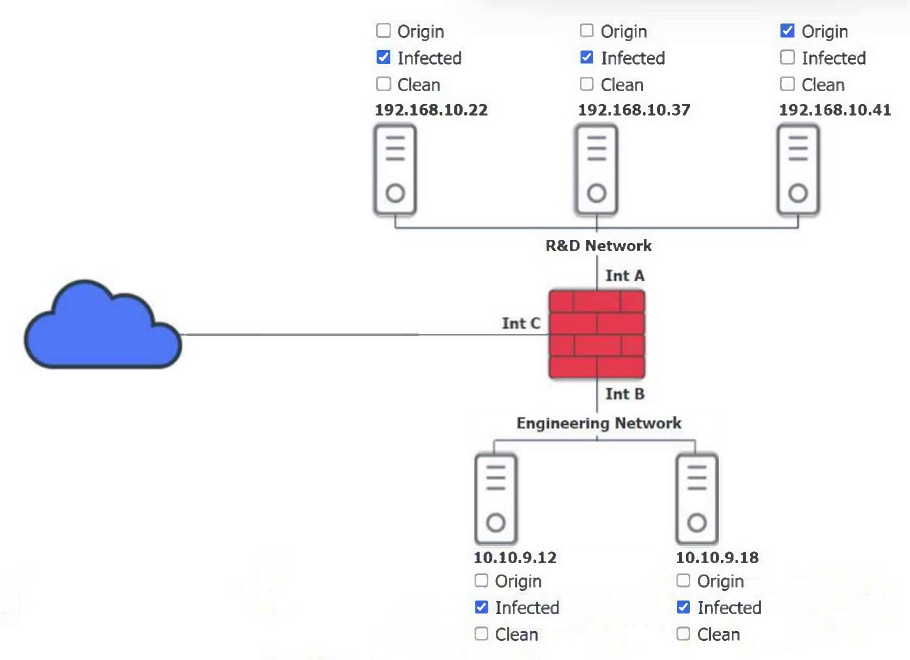
Which of the following is the phase in the incident response process when a security analyst reviews roles and responsibilities?
- A. Preparation
- B. Recovery
- C. Lessons learned
- D. Analysis
After a recent vulnerability scan, a security engineer needs to harden the routers within the corporate network. Which of the following is the most appropriate to disable?
- A. Console access
- B. Routing protocols
- C. VLANs
- D. Web-based administration
A security administrator needs a method to secure data in an environment that includes some form of checks so track any changes. Which of the following should the administrator set up to achieve this goal?
- A. SPF
- B. GPO
- C. NAC
- D. FIM
