We HELP you PASS CompTIA SecurityX (CAS-005) certification, without exam and training!
***Pay after you Pass***
CompTIA SecurityX (CAS-005) Actual Exam Questions
Exam Name: CompTIA SecurityX (CAS-005)
Exam Code Free Dumps: CAS-005
CompTIA SecurityX (CAS-005) Actual Exam 100% Free
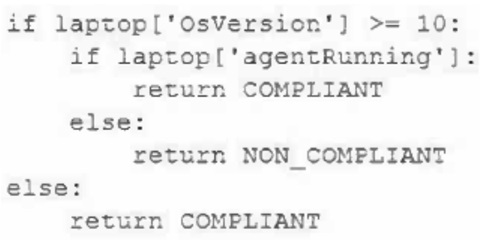
A security engineer is reviewing event logs because an employee successfully connected a personal Windows laptop to the corporate network, which is against company policy. Company policy allows all Windows 10 and 11 laptops to connect to the system as long as the MDM agent installed by IT is running. Only compliant devices can connect, and the logic in the system to evaluate compliant laptops is as follows:
Which of the following most likely occurred when the employee connected a personally owned Windows laptop and was allowed on the network?
- A. The agent was not running on the laptop, which triggered a false positive.
- B. The OS was a valid version, but the MDM agent was not installed, triggering a true positive.
- C. The OS was running a Windows version below 10 and triggered a false negative.
- D. The OS version was higher than 11, and the MDM agent was running, triggering a true negative.
An organization is working to secure its development process to ensure developers cannot deploy artifacts directly into the production environment. Which of the following security practice recommendations would be the best to accomplish this objective?
- A. Implement least privilege access to all systems.
- B. Roll out security awareness training for all users.
- C. Set up policies and systems with separation of duties.
- D. Enforce job rotations for all developers and administrators.
- E. Utilize mandatory vacations for all developers.
- F. Review all access to production systems on a quarterly basis.
A security architect discovers the following while reviewing code for a company’s website: selection = “SELECT Item FROM Catalog WHERE ItemID = ” & Request(“ItemID”)
Which of the following should the security architect recommend?
- A. Client-side processing
- B. Query parameterization
- C. Data normalization
- D. Escape character blocking
- E. URL encoding
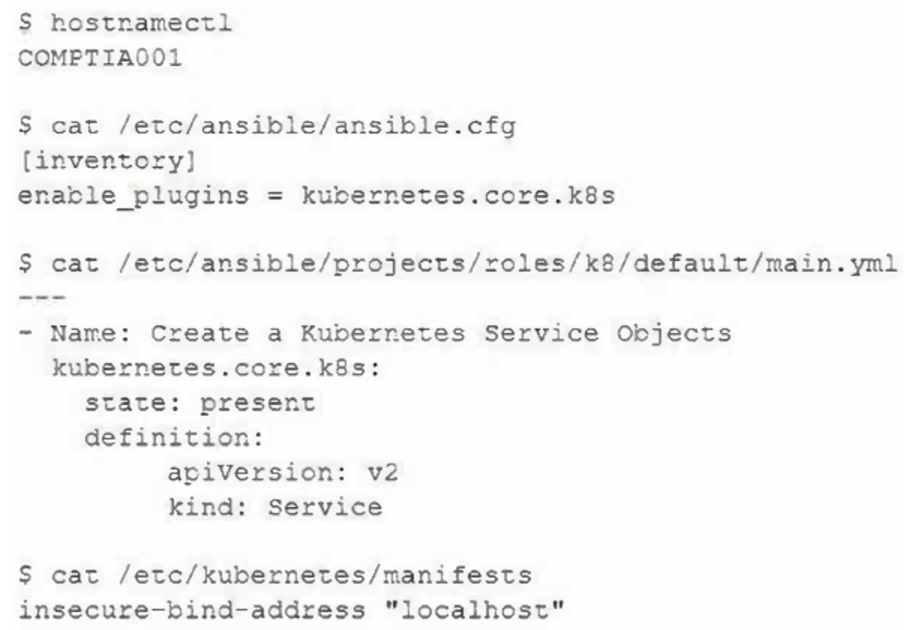
A security architect needs to enable a container orchestrator for DevSecOps and SOAR initiatives. The engineer has discovered that several Ansible YAML files used for the automation of configuration management have the following content:
Which of the following should the engineer do to correct the security issues presented within this content?
- A. Update the kubernetes.core.k8s module to kubernetes.core.k8s_service in the main.yml file.
- B. Update the COMPTIA001 hostname to localhost using the hostnamectl command.
- C. Update the state: present module to state: absent in the main.yml file.
- D. Update or remove the ansible.cfg file.
- E. Update the insecure-bind-address from localhost to the COMPTIA001 in the manifests file.
A CRM company leverages a CSP PaaS service to host and publish Its SaaS product. Recently, a large customer requested that all infrastructure components must meet strict regulatory requirements, including configuration management, patch management, and life-cycle management. Which of the following organizations is responsible for ensuring those regulatory requirements are met?
- A. The CRM company
- B. The CRM company’s customer
- C. The CSP
- D. The regulatory body
Company A is merging with Company B. Company A is a small, local company. Company B has a large, global presence. The two companies have a lot of duplication in their IT systems, processes, and procedures. On the new Chief Information Officer’s (CIO’s) first day, a fire breaks out at Company B’s main data center. Which of the following actions should the CIO take first?
- A. Determine whether the incident response plan has been tested at both companies, and use it to respond.
- B. Review the incident response plans, and engage the disaster recovery plan while relying on the IT leaders from both companies.
- C. Ensure hot, warm, and mobile disaster recovery sites are available, and give an update to the companies’ leadership teams.
- D. Initiate Company A’s IT systems processes and procedures, assess the damage, and perform a BIA.
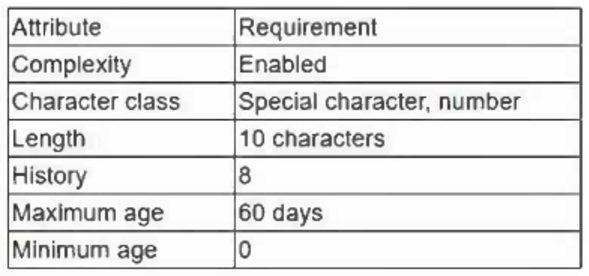
The results of an internal audit indicate several employees reused passwords that were previously included in a published list of compromised passwords.
The company has the following employee password policy:
Which of the following should be implemented to best address the password reuse issue? (Choose two.)
- A. Increase the minimum age to two days.
- B. Increase the history to 20.
- C. Increase the character length to 12.
- D. Add case-sensitive requirements to character class.
- E. Decrease the maximum age to 30 days.
- F. Remove the complexity requirements.
- G. Increase the maximum age to 120 days.
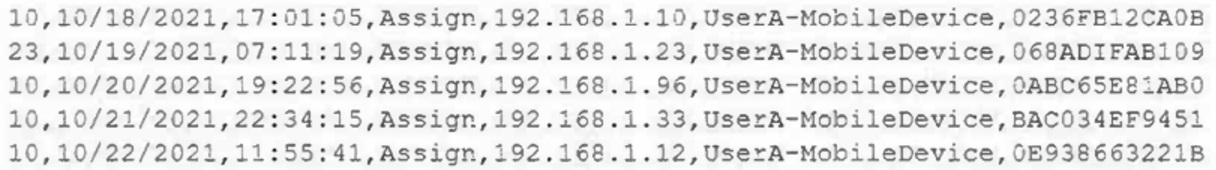
A mobile administrator is reviewing the following mobile device DHCP logs to ensure the proper mobile settings are applied to managed devices:
Which of the following mobile configuration settings is the mobile administrator verifying?
- A. Service set identifier authentication
- B. Wireless network auto joining
- C. 802.1X with mutual authentication
- D. Association MAC address randomization
A security analyst is investigating a possible insider threat incident that involves the use of an unauthorized USB from a shared account to exfiltrate data. The event did not create an alert. The analyst has confirmed the USB hardware ID is not on the device allow list, but has not yet confirmed the owner of the USB device. Which of the following actions should the analyst take next?
- A. Classify the incident as a false positive.
- B. Classify the incident as a false negative.
- C. Classify the incident as a true positive.
- D. Classify the incident as a true negative.
Which of the following security features do email signatures provide?
- A. Non-repudiation
- B. Body encryption
- C. Code signing
- D. Sender authentication
- E. Chain of custody
A software development company wants to ensure that users can confirm the software is legitimate when installing it. Which of the following is the best way for the company to achieve this security objective?
- A. Code signing
- B. Non-repudiation
- C. Key escrow
- D. Private keys
While performing mandatory monthly patch updates on a production application server, the security analyst reports an instance of buffer overflow for a new application that was migrated to the cloud and is also publicly exposed. Security policy requires that only internal users have access to the application. Which of the following should the analyst implement to mitigate the issues reported? (Choose two.)
- A. Configure firewall rules to block all external traffic.
- B. Enable input validation for all fields.
- C. Enable automatic updates to be installed on all servers.
- D. Configure the security group to enable external traffic.
- E. Set up a DLP policy to alert for exfiltration on all application servers.
- F. Enable nightly vulnerability scans.
PKI can be used to support security requirements in the change management process. Which of the following capabilities does PKI provide for messages?
- A. Non-repudiation
- B. Confidentiality
- C. Delivery receipts
- D. Attestation
Several unlabeled documents in a cloud document repository contain cardholder information. Which of the following configuration changes should be made to the DLP system to correctly label these documents in the future?
- A. Digital rights management
- B. Network traffic decryption
- C. Regular expressions
- D. Watermarking
A systems administrator at a web-hosting provider has been tasked with renewing the public certificates of all customer sites. Which of the following would best support multiple domain names while minimizing the amount of certificates needed?
- A. OCSP
- B. CRL
- C. SAND. CA
Which of the following best explain why organizations prefer to utilize code that is digitally signed? (Choose two.)
- A. It provides origin assurance.
- B. It verifies integrity.
- C. It provides increased confidentiality.
- D. It integrates with DRMs.
- E. It verifies the recipient’s identity.
- F. It ensures the code is free of malware.
A security engineer evaluates the overall security of a custom mobile gaming application and notices that developers are bringing in a large number of open-source packages without appropriate patch management. Which of the following would the engineer most likely recommend for uncovering known vulnerabilities in the packages?
- A. Leverage an exploitation framework to uncover vulnerabilities.
- B. Use fuzz testing to uncover potential vulnerabilities in the application.
- C. Utilize a software composition analysis tool to report known vulnerabilities.
- D. Reverse engineer the application to look for vulnerable code paths.
- E. Analyze the use of an HTTP intercepting proxy to dynamically uncover issues.
Updating