
Pass Microsoft AZ-104 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
You have an Azure App Service app named App1 that contains two running instances.
You have an autoscale rule configured as shown in the following exhibit.
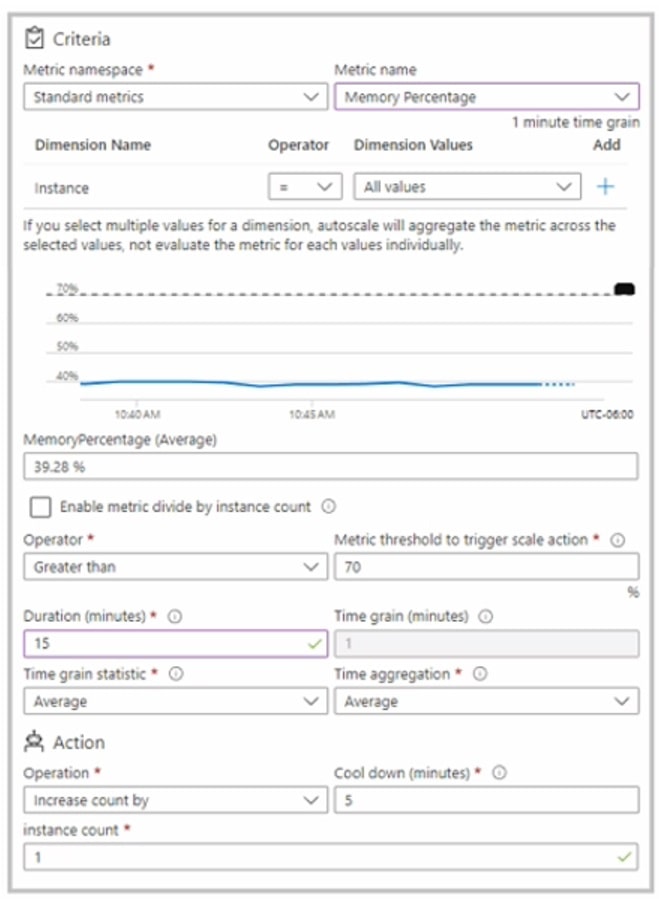
For the Instance limits scale condition setting, you set Maximum to 5.
During a 30-minute period, App1 uses 80 percent of the available memory.
What is the maximum number of instances for App1 during the 30-minute period?
- A. 2
- B. 3
- C. 4
- D. 5
HOTSPOT –
You have a virtual network named VNET1 that contains the subnets shown in the following table:
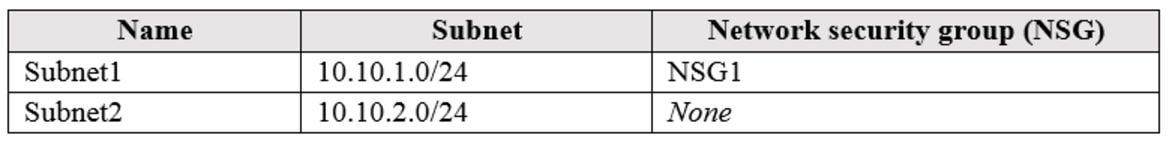
You have Azure virtual machines that have the network configurations shown in the following table:
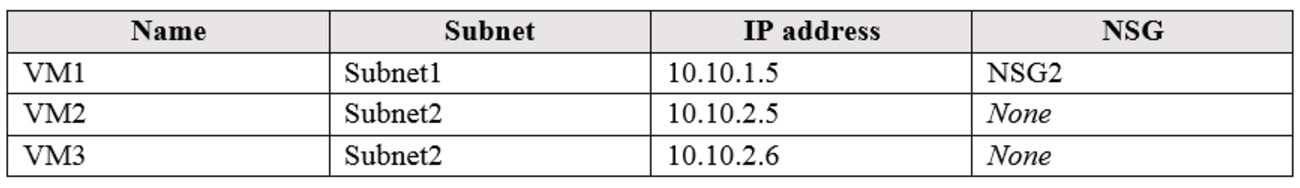
For NSG1, you create the inbound security rule shown in the following table:

For NSG2, you create the inbound security rule shown in the following table:

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
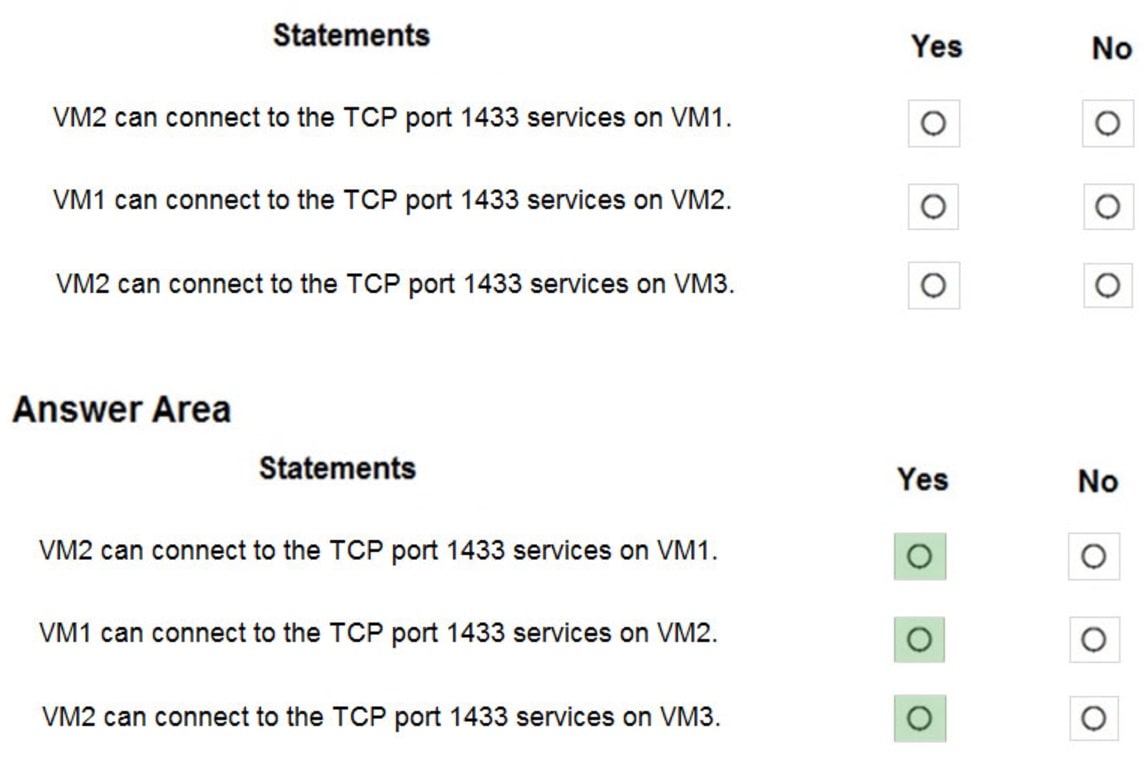
Box 1: Yes –
The inbound security rule for NSG1 allows TCP port 1433 from 10.10.2.0/24 (or Subnet2 where VM2 and VM3 are located) to 10.10.1.0/24 (or Subnet1 where
VM1 is located) while the inbound security rule for NSG2 blocks TCP port 1433 from 10.10.2.5 (or VM2) to 10.10.1.5 (or VM1). However, the NSG1 rule has a higher priority (or lower value) than the NSG2 rule.
Box 2: Yes –
No rule explicitly blocks communication from VM1. The default rules, which allow communication, are thus applied.
Box 3: Yes –
No rule explicitly blocks communication between VM2 and VM3 which are both on Subnet2. The default rules, which allow communication, are thus applied.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/security-overview
HOTSPOT
–
Case study
–
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
–
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
–
A Datum Corporation is consulting firm that has a main office in Montreal and branch offices in Seattle and New York.
Existing Environment
–
Azure Environment
–
A Datum has an Azure subscription that contains three resource groups named RG1, RG2, and RG3.
The subscription contains the storage accounts shown in the following table.
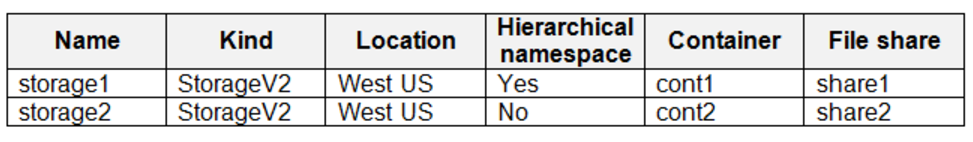
The subscription contains the virtual machines shown in the following table.
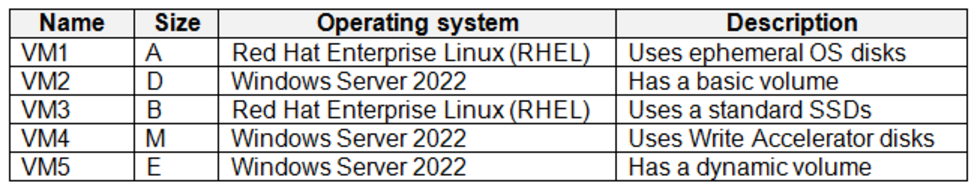
The subscription has an Azure container registry that contains the images shown in the following table.
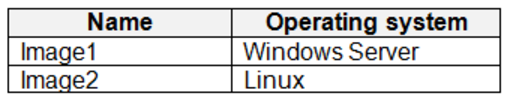
The subscription contains the resources shown in the following table.
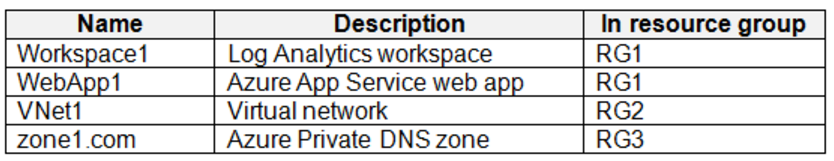
Azure Key Vault
–
The subscription contains an Azure key vault named Vault1.
Vault1 contains the certificates shown in the following table.
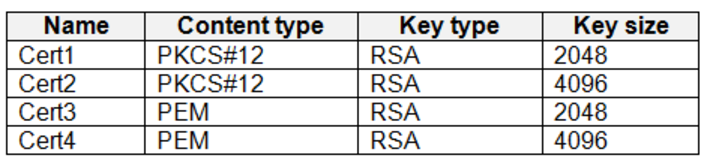
Vault1 contains the keys shown in the following table.
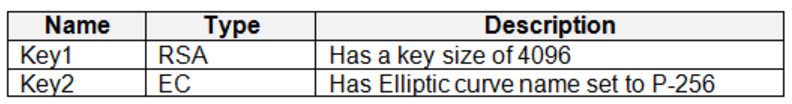
Microsoft Entra Environment
–
A Datum has a Microsoft Entra tenant named adatum.com that is linked to the Azure subscription and contains the users shown in the following table.
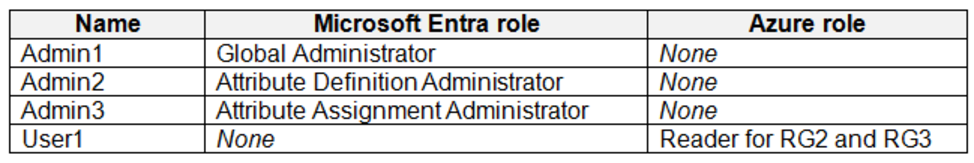
The tenant contains the groups shown in the following table.
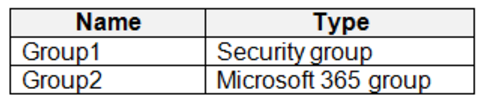
The adatum.com tenant has a custom security attribute named Attribute1.
Planned Changes
–
ADatum plans to implement the following changes:
• Configure a data collection rule (DCR) named DCR1 to collect only system events that have an event ID of 4648 from VM2 and VM4.
• In storage1, create a new container named cont2 that has the following access policies:
o Three stored access policies named Stored1, Stored2, and Stored3
o A legal hold for immutable blob storage
• Whenever possible, use directories to organize storage account content.
• Grant User1 the permissions required to link Zone1 to VNet1.
• Assign Attribute1 to supported adatum.com resources.
• In storage2, create an encryption scope named Scope1.
• Deploy new containers by using Image1 or Image2.
Technical Requirements
–
ADatum must meet the following technical requirements:
• Use TLS for WebApp1.
• Follow the principle of least privilege.
• Grant permissions at the required scope only.
• Ensure that Scope1 is used to encrypt storage services.
• Use Azure Backup to back up cont1 and share1 as frequently as possible.
• Whenever possible, use Azure Disk Encryption and a key encryption key (KEK) to encrypt the virtual machines.
You need to configure encryption for the virtual machines. The solution must meet the technical requirements.
Which virtual machines can you encrypt?
- A. VM1 and VM3
- B. VM4 and VM5
- C. VM2 and VM3
- D. VM2 and VM4
HOTSPOT –
You have an Azure subscription named Subscription1.
Subscription1 contains the virtual machines in the following table:
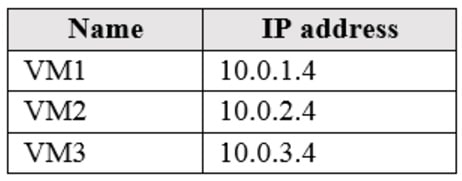
Subscription1 contains a virtual network named VNet1 that has the subnets in the following table:
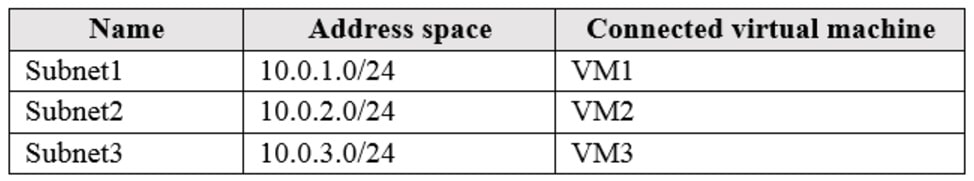
VM3 has multiple network adapters, including a network adapter named NIC3. IP forwarding is enabled on NIC3. Routing is enabled on VM3.
You create a route table named RT1 that contains the routes in the following table:
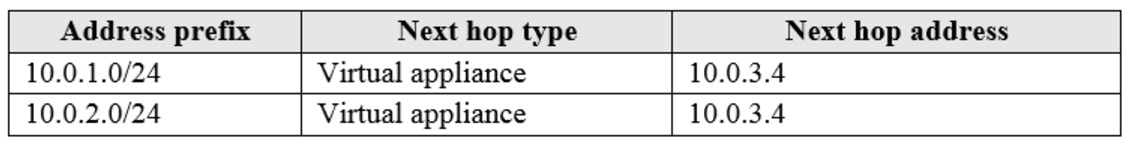
You apply RT1 to Subnet1 and Subnet2.
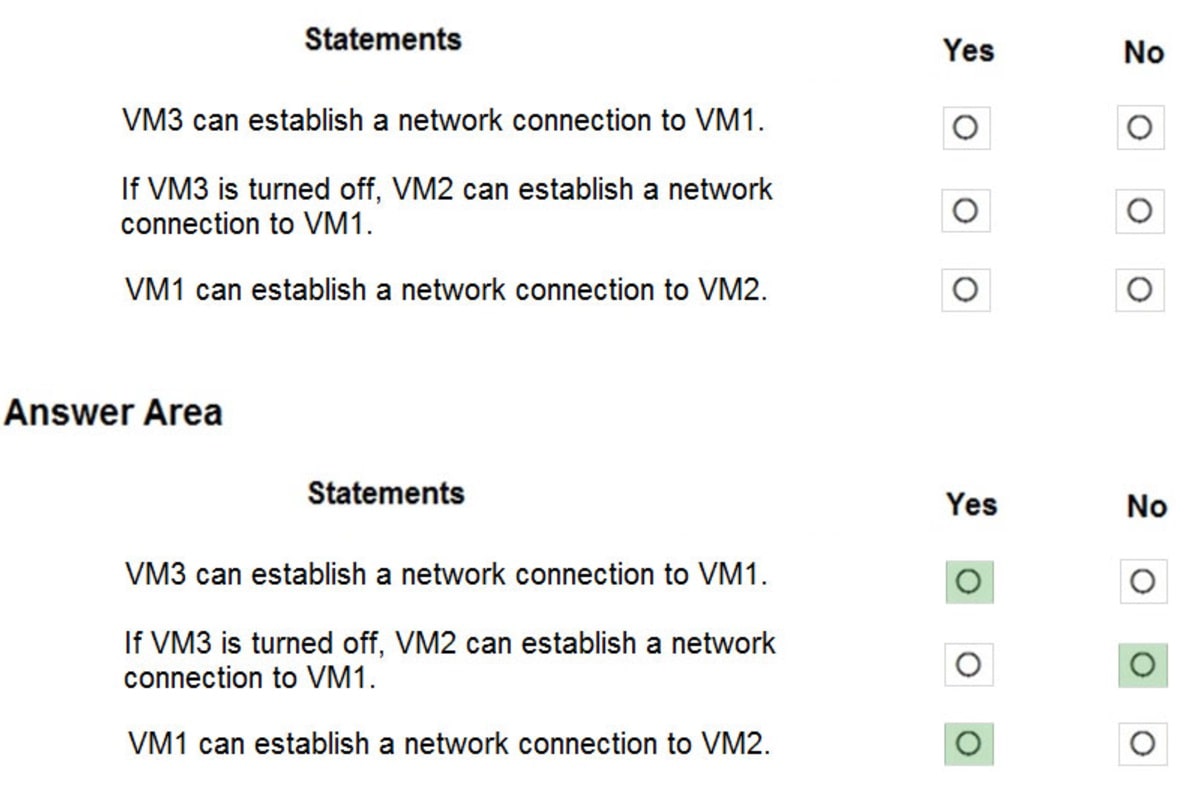
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
IP forwarding enables the virtual machine a network interface is attached to:
✑ Receive network traffic not destined for one of the IP addresses assigned to any of the IP configurations assigned to the network interface.
Send network traffic with a different source IP address than the one assigned to one of a network interface’s IP configurations.

The setting must be enabled for every network interface that is attached to the virtual machine that receives traffic that the virtual machine needs to forward. A virtual machine can forward traffic whether it has multiple network interfaces or a single network interface attached to it.
Box 1: Yes –
The routing table allows connections from VM3 to VM1 and VM2. And as IP forwarding is enabled on VM3, VM3 can connect to VM1.
Box 2: No –
VM3, which has IP forwarding, must be turned on, in order for VM2 to connect to VM1.
Box 3: Yes –
The routing table allows connections from VM1 and VM2 to VM3. IP forwarding on VM3 allows VM1 to connect to VM2 via VM3.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/virtual-networks-udr-overview https://www.quora.com/What-is-IP-forwarding
Your on-premises network contains a VPN gateway.
You have an Azure subscription that contains the resources shown in the following table.
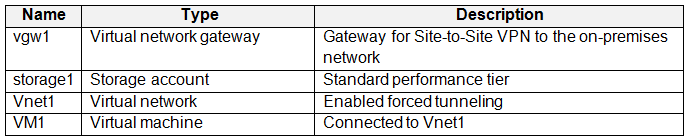
You need to ensure that all the traffic from VM1 to storage1 travels across the Microsoft backbone network.
What should you configure?
- A. Azure Application Gateway
- B. service endpoints
- C. a network security group (NSG)
- D. Azure Peering Service
HOTSPOT
–
Case study
–
This is a case study. Case studies are not timed separately. You can use as much exam time as you would like to complete each case. However, there may be additional case studies and sections on this exam. You must manage your time to ensure that you are able to complete all questions included on this exam in the time provided.
To answer the questions included in a case study, you will need to reference information that is provided in the case study. Case studies might contain exhibits and other resources that provide more information about the scenario that is described in the case study. Each question is independent of the other questions in this case study.
At the end of this case study, a review screen will appear. This screen allows you to review your answers and to make changes before you move to the next section of the exam. After you begin a new section, you cannot return to this section.
To start the case study
–
To display the first question in this case study, click the Next button. Use the buttons in the left pane to explore the content of the case study before you answer the questions. Clicking these buttons displays information such as business requirements, existing environment, and problem statements. If the case study has an All Information tab, note that the information displayed is identical to the information displayed on the subsequent tabs. When you are ready to answer a question, click the Question button to return to the question.
Overview
–
A Datum Corporation is consulting firm that has a main office in Montreal and branch offices in Seattle and New York.
Existing Environment
–
Azure Environment
–
A Datum has an Azure subscription that contains three resource groups named RG1, RG2, and RG3.
The subscription contains the storage accounts shown in the following table.

The subscription contains the virtual machines shown in the following table.

The subscription has an Azure container registry that contains the images shown in the following table.

The subscription contains the resources shown in the following table.

Azure Key Vault
–
The subscription contains an Azure key vault named Vault1.
Vault1 contains the certificates shown in the following table.

Vault1 contains the keys shown in the following table.

Microsoft Entra Environment
–
A Datum has a Microsoft Entra tenant named adatum.com that is linked to the Azure subscription and contains the users shown in the following table.

The tenant contains the groups shown in the following table.

The adatum.com tenant has a custom security attribute named Attribute1.
Planned Changes
–
ADatum plans to implement the following changes:
• Configure a data collection rule (DCR) named DCR1 to collect only system events that have an event ID of 4648 from VM2 and VM4.
• In storage1, create a new container named cont2 that has the following access policies:
o Three stored access policies named Stored1, Stored2, and Stored3
o A legal hold for immutable blob storage
• Whenever possible, use directories to organize storage account content.
• Grant User1 the permissions required to link Zone1 to VNet1.
• Assign Attribute1 to supported adatum.com resources.
• In storage2, create an encryption scope named Scope1.
• Deploy new containers by using Image1 or Image2.
Technical Requirements
–
ADatum must meet the following technical requirements:
• Use TLS for WebApp1.
• Follow the principle of least privilege.
• Grant permissions at the required scope only.
• Ensure that Scope1 is used to encrypt storage services.
• Use Azure Backup to back up cont1 and share1 as frequently as possible.
• Whenever possible, use Azure Disk Encryption and a key encryption key (KEK) to encrypt the virtual machines.
You need to implement the planned changes for the storage account content.
Which containers and file shares can you use to organize the content?
- A. share1 only
- B. cont1 and share1 only
- C. share1 and share2 only
- D. cont1, share1, and share2 only
- E. cont1, cont2, share1, and share2
You have an Azure AD tenant named contoso.com.
You have an Azure subscription that contains an Azure App Service web app named App1 and an Azure key vault named KV1. KV1 contains a wildcard certificate for contoso.com.
You have a user named user1@contoso.com that is assigned the Owner role for App1 and KV1.
You need to configure App1 to use the wildcard certificate of KV1.
What should you do first?
- A. Create an access policy for KV1 and assign the Microsoft Azure App Service principal to the policy.
- B. Assign a managed user identity to App1.
- C. Configure KV1 to use the role-based access control (RBAC) authorization system.
- D. Create an access policy for KV1 and assign the policy to User1.
Your on-premises network contains an SMB share named Share1.
You have an Azure subscription that contains the following resources:
– A web app named webapp1
– A virtual network named VNET1
You need to ensure that webapp1 can connect to Share1.
What should you deploy?
- A. an Azure Application Gateway
- B. an Azure Active Directory (Azure AD) Application Proxy
- C. an Azure Virtual Network Gateway
You have an Azure subscription.
You plan to deploy the resources shown in the following table.
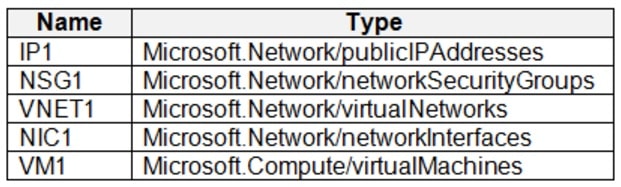
You need to create a single Azure Resource Manager (ARM) template that will be used to deploy the resources.
Which resource should be added to the dependsOn section for VM1?
- A. VNET1
- B. NIC1
- C. IP1
- D. NSG1
You plan to deploy several Azure virtual machines that will run Windows Server 2019 in a virtual machine scale set by using an Azure Resource Manager template.
You need to ensure that NGINX is available on all the virtual machines after they are deployed.
What should you use?
- A. the Publish-AzVMDscConfiguration cmdlet
- B. Azure Application Insights
- C. Azure Custom Script Extension
- D. the New-AzConfigurationAssignement cmdlet
