
Pass 300-710 SNCF in Just 3 Days – Stress-Free!
Get your 300-710 Securing Networks with Cisco Firepower certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
Question 91
What is the maximum bit size that Cisco FMC supports for HTTPS certificates?
- A. 1024
- B. 8192
- C. 4096
- D. 2048
Correct Answer: C
Question 92
Which limitation applies to Cisco FMC dashboards in a multi-domain environment?
- A. Child domains are able to view but not edit dashboards that originate from an ancestor domain.
- B. Child domains have access to only a limited set of widgets from ancestor domains.
- C. Only the administrator of the top ancestor domain is able to view dashboards.
- D. Child domains are not able to view dashboards that originate from an ancestor domain.
Correct Answer: D
Question 93
Which two considerations must be made when deleting and re-adding devices while managing them via Cisco FMC? (Choose two.)
- A. An option to re-apply NAT and VPN policies during registration is available, so users do not need to re-apply the policies after registration is completed.
- B. Before re-adding the device in Cisco FMC, the manager must be added back.
- C. Once a device has been deleted, it must be reconfigured before it is re-added to the Cisco FMC.
- D. The Cisco FMC web interface prompts users to re-apply access control policies.
- E. There is no option to re-apply NAT and VPN policies during registration available, so users need to re-apply the policies after registration is completed.
Correct Answer: D, E
Question 94
What is a behavior of a Cisco FMC database purge?
- A. User login and history data are removed from the database if the User Activity check box is selected.
- B. Data is recovered from the device.
- C. The appropriate process is restarted.
- D. The specified data is removed from Cisco FMC and kept for two weeks.
Correct Answer: C
Question 95
Which two packet captures does the FTD LINA engine support? (Choose two.)
- A. Layer 7 network ID
- B. Source IP
- C. Application ID
- D. Dynamic firewall importing
- E. Protocol
Correct Answer: B, E
Question 96
An engineer currently has a Cisco FTD device registered to the Cisco FMC and is assigned the address of 10.10.50.12. The organization is upgrading the addressing schemes and there is a requirement to convert the addresses to a format that provides an adequate amount of addresses on the network. What should the engineer do to ensure that the new addressing takes effect and can be used for the Cisco FTD to Cisco FMC connection?
- A. Update the IP addresses from IPv4 to IPv6 without deleting from Cisco FMC.
- B. Format and reregister the device to Cisco FMC.
- C. Cisco FMC does not support devices that use IPv4 IP addresses.
- D. Delete and reregister the device to Cisco FMC.
Correct Answer: D
Question 97
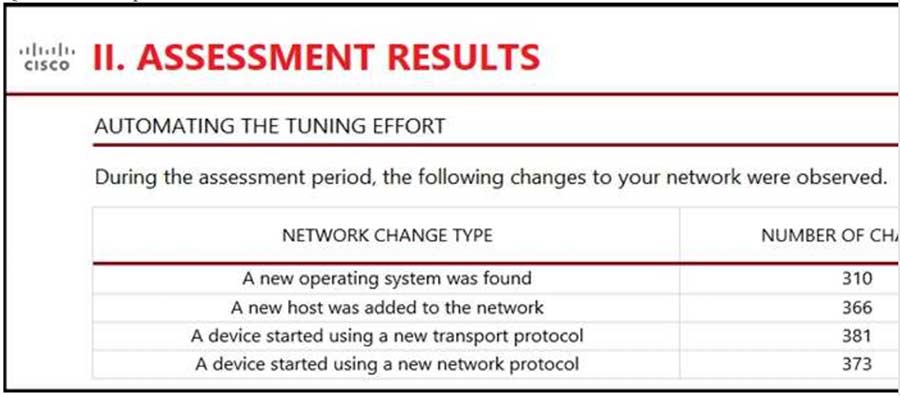
Refer to the exhibit. An engineer is analyzing the Attacks Risk Report and finds that there are over 300 instances of new operating systems being seen on the network. How is the Firepower configuration updated to protect these new operating systems?
- A. The administrator manually updates the policies.
- B. The administrator requests a Remediation Recommendation Report from Cisco Firepower.
- C. Cisco Firepower gives recommendations to update the policies.
- D. Cisco Firepower automatically updates the policies.
Correct Answer: C
Question 98
After using Firepower for some time and learning about how it interacts with the network, an administrator is trying to correlate malicious activity with a user. Which widget should be configured to provide this visibility on the Cisco Firepower dashboards?
- A. Current Sessions
- B. Correlation Events
- C. Current Status
- D. Custom Analysis
Correct Answer: B
Question 99
An engineer is troubleshooting application failures through an FTD deployment. While using the FMC CLI it has been determined that the traffic in question is not matching the desired policy. What should be done to correct this?
- A. Use the system support firewall-engine-debug command to determine which rules the traffic is matching and modify the rule accordingly.
- B. Use the system support firewall-engine-dump-user-identity-data command to change the policy and allow the application through the firewall.
- C. Use the system support application-identification-debug command to determine which rules the traffic is matching and modify the rule accordingly.
- D. Use the system support network-options command to fine-tune the policy.
Correct Answer: A
Question 100
An engineer has been asked to show application usages automatically on a monthly basis and send the information to management. What mechanism should be used to accomplish this task?
- A. Reports
- B. Context Explorer
- C. Dashboards
- D. Event Viewer
Correct Answer: A
