
Pass 300-710 SNCF in Just 3 Days – Stress-Free!
Get your 300-710 Securing Networks with Cisco Firepower certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
Question 101
A network administrator is configuring SNORT inspection policies and is seeing failed deployment messages in Cisco FMC. What information should the administrator generate for Cisco TAC to help troubleshoot?
- A. A x€troubleshoota€ file for the device in question.
- B. A x€show techi€ file for the device in question.
- C. A setroubleshoots€ file for the Cisco FMC.
- D. A x€show tech€ for the Cisco FMC.
Correct Answer: C
Question 102
An engineer is troubleshooting a device that cannot connect to a web server. The connection is initiated from the Cisco FTD inside interface and attempting to reach 10.0.1.100 over the non-standard port of 9443. The host the engineer is attempting the connection from is at the IP address of 10.20.10.20. In order to determine what is happening to the packets on the network, the engineer decides to use the FTD packet capture tool. Which capture configuration should be used to gather the information needed to troubleshoot the issue?
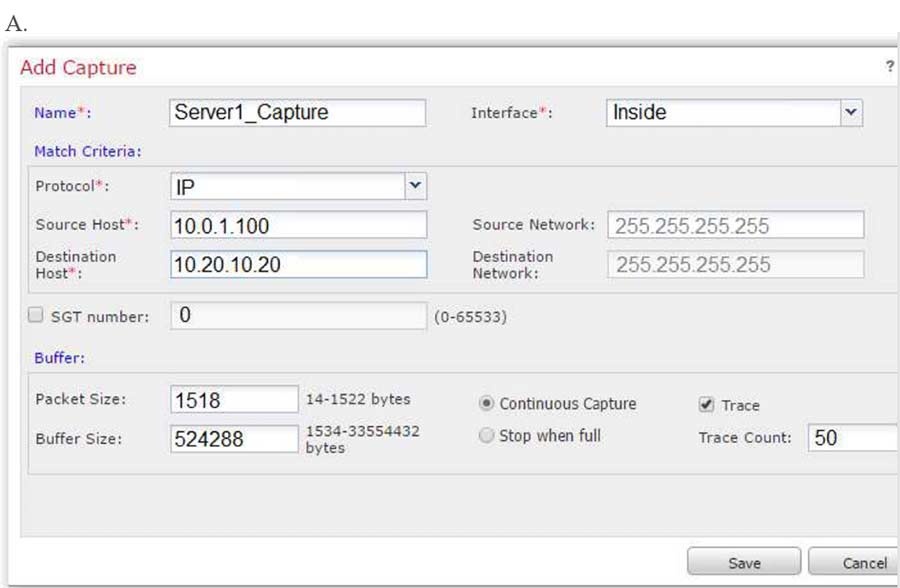
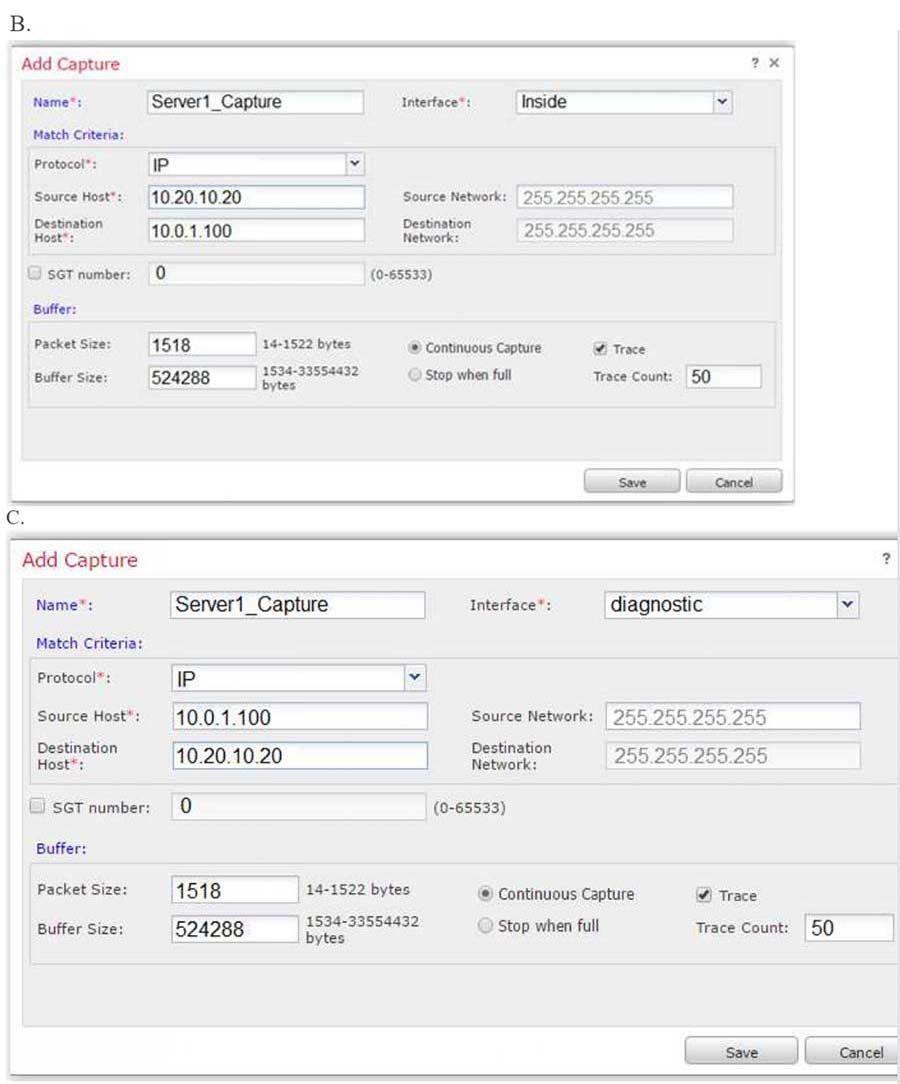
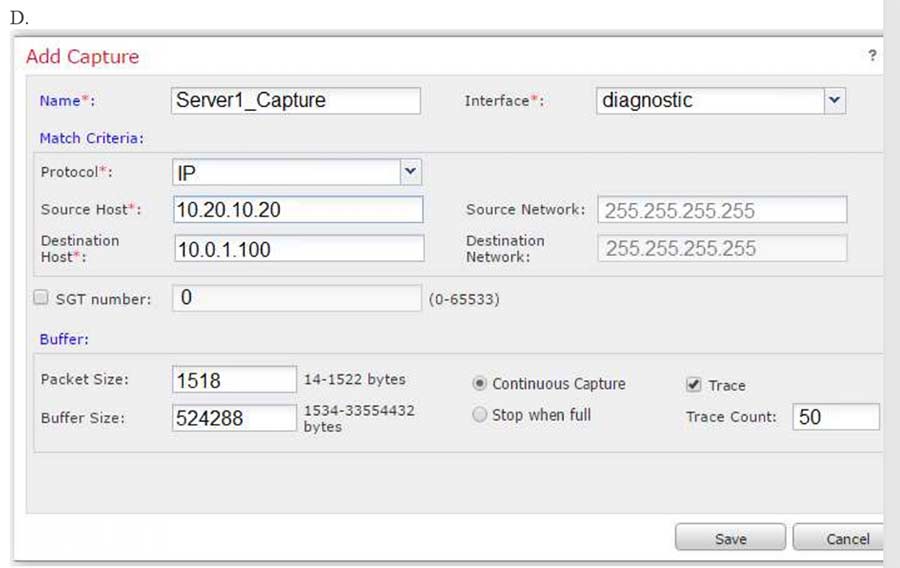
Correct Answer: B
Question 103
A network engineer is receiving reports of users randomly getting disconnected from their corporate applications which traverse the data center FTD appliance. Network monitoring tools show that the FTD appliance utilization is peaking above 90% of total capacity. What must be done in order to further analyze this issue?
- A. Use the Packet Export feature to save data onto external drives.
- B. Use the Packet Capture feature to collect real-time network traffic.
- C. Use the Packet Tracer feature for traffic policy analysis.
- D. Use the Packet Analysis feature for capturing network data.
Correct Answer: B
Question 104
An administrator is attempting to remotely log into a switch in the data center using SSH and is unable to connect. How does the administrator confirm that traffic is reaching the firewall?
- A. By performing a packet capture on the firewall.
- B. By attempting to access it from a different workstation.
- C. By running Wireshark on the administrator’s PC.
- D. By running a packet tracer on the firewall.
Correct Answer: D
Question 105
IT management is asking the network engineer to provide high-level summary statistics of the Cisco FTD appliance in the network. The business is approaching a peak season so the need to maintain business uptime is high. Which report type should be used to gather this information?
- A. Risk Report
- B. SNMP Report
- C. Standard Report
- D. Malware Report
Correct Answer: C
Question 106
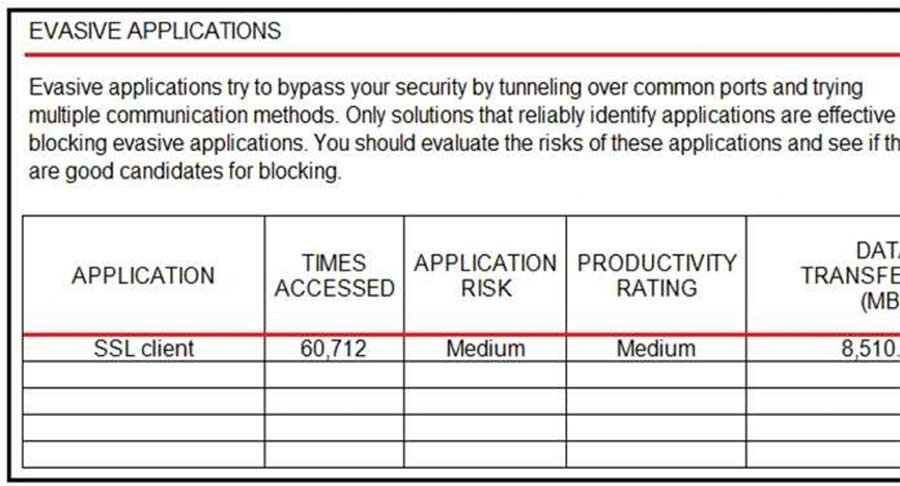
Refer to the exhibit. An administrator is looking at some of the reporting capabilities for Cisco Firepower and noticed this section of the Network Risk Report showing a lot of SSL activity that could be used for evasion. Which action will mitigate this risk?
- A. Use SSL decryption to analyze the packets.
- B. Use Cisco Tetration to track SSL connections to servers.
- C. Use encrypted traffic analytics to detect attacks.
- D. Use Cisco AMP for Endpoints to block all SSL connections.
Correct Answer: A
Question 107
An administrator is setting up Cisco FirePower to send data to the Cisco Stealthwatch appliances. The NetFlow_Set Parameters object is already created, but NetFlow is not being sent to the flow collector. What must be done to prevent this from occurring?
- A. Create a service identifier to enable the NetFlow service.
- B. Add the NetFlow_Send_Destination object to the configuration.
- C. Create a Security Intelligence object to send the data to Cisco Stealthwatch.
- D. Add the NetFlow_Add_Destination object to the configuration.
Correct Answer: D
Question 108
With a recent summer time change, system logs are showing activity that occurred to be an hour behind real time. Which action should be taken to resolve this issue?
- A. Manually adjust the time to the correct hour on all managed devices.
- B. Configure the system clock settings to use NTP with Daylight Savings checked.
- C. Configure the system clock settings to use NTP.
- D. Manually adjust the time to the correct hour on the Cisco FMC.
Correct Answer: C
Question 109
A network administrator notices that SI events are not being updated. The Cisco FTD device is unable to load all of the SI event entries and traffic is not being blocked as expected. What must be done to correct this issue?
- A. Restart the affected devices in order to reset the configurations.
- B. Redeploy configurations to affected devices so that additional memory is allocated to the SI module.
- C. Replace the affected devices with devices that provide more memory.
- D. Manually update the SI event entries to ensure that the appropriate traffic is blocked.
Correct Answer: B
Question 110
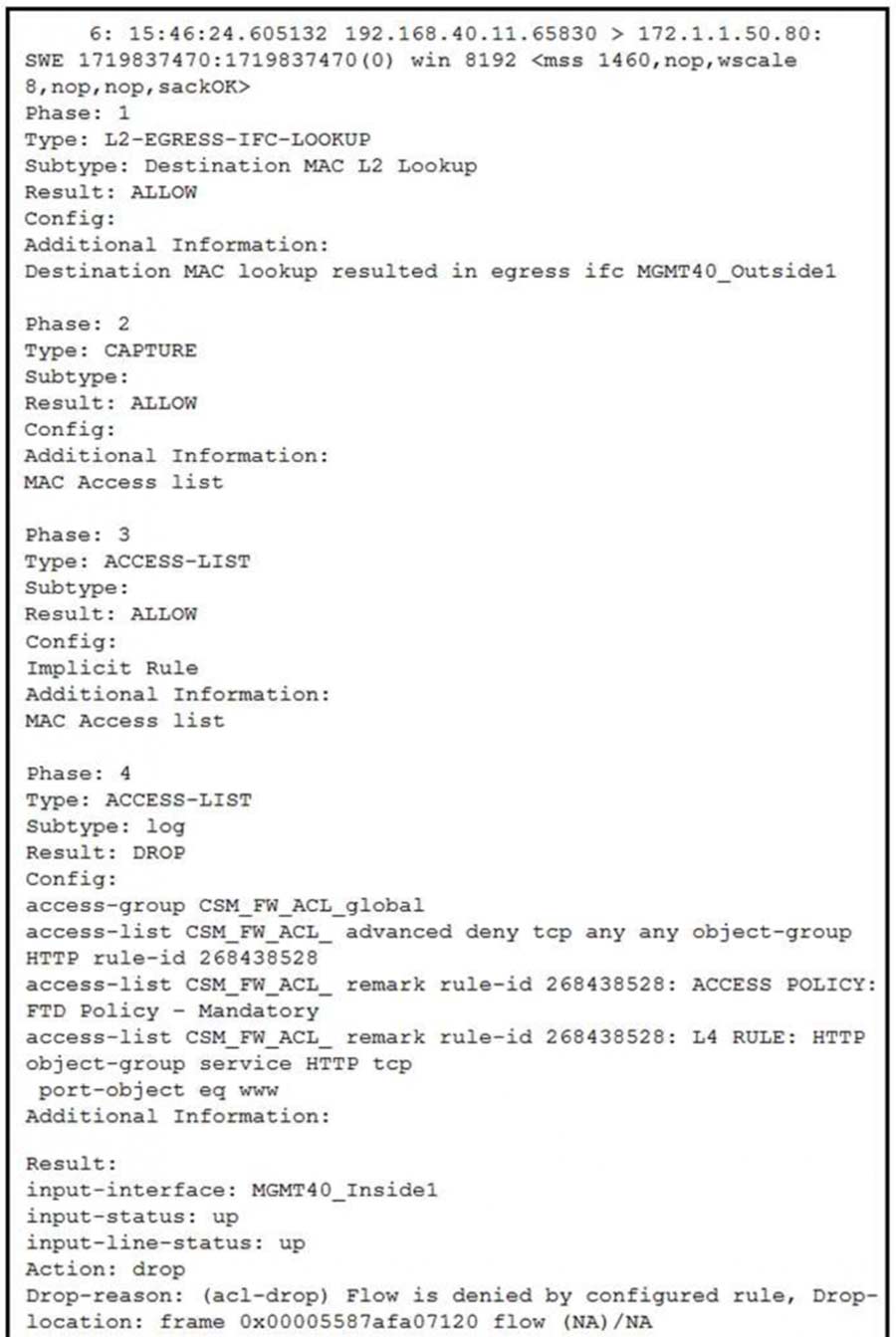
Refer to the exhibit. What must be done to fix access to this website while preventing the same communication to all other websites?
- A. Create an intrusion policy rule to have Snort allow port 80 to only 172.1.1.50.
- B. Create an intrusion policy rule to have Snort allow port 443 to only 172.1.1.50.
- C. Create an access control policy rule to allow port 443 to only 172.1.1.50.
- D. Create an access control policy rule to allow port 80 to only 172.1.1.50.
Correct Answer: D
