
Pass 300-710 SNCF in Just 3 Days – Stress-Free!
Get your 300-710 Securing Networks with Cisco Firepower certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
Question 161
A security engineer is configuring a remote Cisco FTD that has limited resources and internet bandwidth. Which malware action and protection option should be configured to reduce the requirement for cloud lookups?
- A. Block File action and local malware analysis
- B. Malware Cloud Lookup and dynamic analysis
- C. Block Malware action and dynamic analysis
- D. Block Malware action and local malware analysis
Correct Answer: D
Question 162
An administrator must use Cisco FMC to install a backup route within the Cisco FTD to route traffic in case of a routing failure with the primary route. Which action accomplishes this task?
- A. Install the static backup route and modify the metric to be less than the primary route
- B. Use a default route in the FMC instead of having multiple routes contending for priority
- C. Configure EIGRP routing on the FMC to ensure that dynamic routes are always updated
- D. Create the backup route and use route tracking on both routes to a destination IP address in the network
Correct Answer: D
Question 163
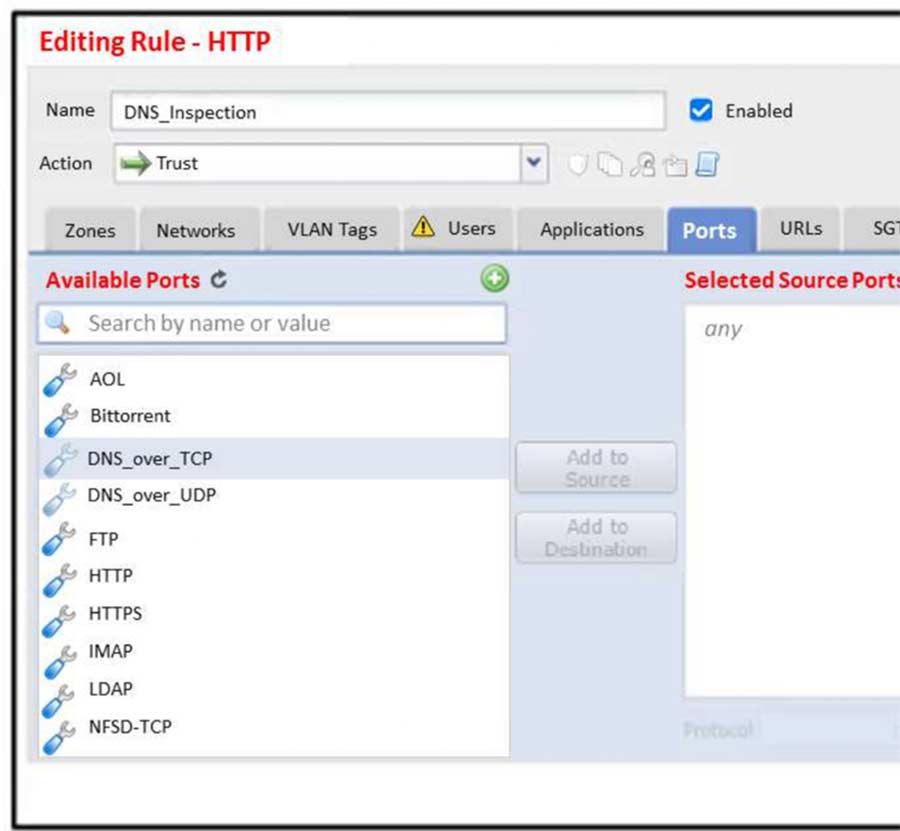
An engineer is modifying an access control policy to add a rule to inspect all DNS traffic that passes through the firewall. After making the change and deploying the policy, they see that DNS traffic is not being inspected by the Snort engine. What is the problem?
- A. The action of the rule is set to trust instead of allow.
- B. The rule is configured with the wrong setting for the source port.
- C. The rule must define the source network for inspection as well as the port.
- D. The rule must specify the security zone that originates the traffic.
Correct Answer: C
Question 164
A network administrator configured a NAT policy that translates a public IP address to an internal web server IP address. An access policy has also been created that allows any source to reach the public IP address on port 80. The web server is still not reachable from the Internet on port 80. Which configuration change is needed?
- A. The NAT policy must be modified to translate the source IP address as well as destination address.
- B. The access policy must allow traffic to the internal web server IP address.
- C. The intrusion policy must be disabled for port 80.
- D. The access policy rule must be configured for the action trust.
Correct Answer: B
Question 165
An administrator is adding a new URL-based category feed to the Cisco FMC for use within the policies. The intelligence source does not use STIX, but instead uses a .txt file format. Which action ensures that regular updates are provided?
- A. Add a URL source and select the flat file type within Cisco FMC.
- B. Add a TAXII feed source and input the URL for the feed.
- C. Upload the .txt file and configure automatic updates using the embedded URL.
- D. Convert the .txt file to STIX and upload it to the Cisco FMC.
Correct Answer: C
Question 166
An engineer is configuring Cisco FMC and wants to limit the time allowed for processing packets through the interface. However, if the time is exceeded, the configuration must allow packets to bypass detection. What must be configured on the Cisco FMC to accomplish this task?
- A. Cisco ISE Security Group Tag
- B. Automatic Application Bypass
- C. Inspect Local Traffic Bypass
- D. Fast-Path Rules Bypass
Correct Answer: B
Question 167
An engineer must define a URL object on Cisco FMC. What is the correct method to specify the URL without performing SSL inspection?
- A. Include all URLs from CRL Distribution Points.
- B. Use Subject Common Name value.
- C. Specify all subdomains in the object group.
- D. Specify the protocol in the object.
Correct Answer: B
Question 168
An organization recently implemented a transparent Cisco FTD in their network. They must ensure that the device does not respond to insecure SSL/TLS protocols. Which action accomplishes this task?
- A. Modify the device’s settings using the device management feature within Cisco FMC to force only secure protocols.
- B. Use the Cisco FTD platform policy to change the minimum SSL version on the device to TLS 1.2.
- C. Enable the UCAPL/CC compliance on the device to support only the most secure protocols available.
- D. Configure a FlexConfig object to disable any insecure TLS protocols on the Cisco FTD device.
Correct Answer: B
Question 169
A network administrator is migrating from a Cisco ASA to a Cisco FTD. EIGRP is configured on the Cisco ASA but it is not available in the Cisco FMC. Which action must the administrator take to enable this feature on the Cisco FTD?
- A. Configure EIGRP parameters using FlexConfig objects.
- B. Add the command feature eigrp via the FTD CLL.
- C. Create a custom variable set and enable the feature in the variable set.
- D. Enable advanced configuration options in the FMC.
Correct Answer: A
Question 170
A Cisco FMC administrator wants to configure fast-pathing of trusted network traffic to increase performance. In which type of policy would the administrator configure this feature?
- A. Network Analysis policy
- B. Identity policy
- C. Prefilter policy
- D. Intrusion policy
Correct Answer: C
