
Pass 300-710 SNCF in Just 3 Days – Stress-Free!
Get your 300-710 Securing Networks with Cisco Firepower certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
Question 171
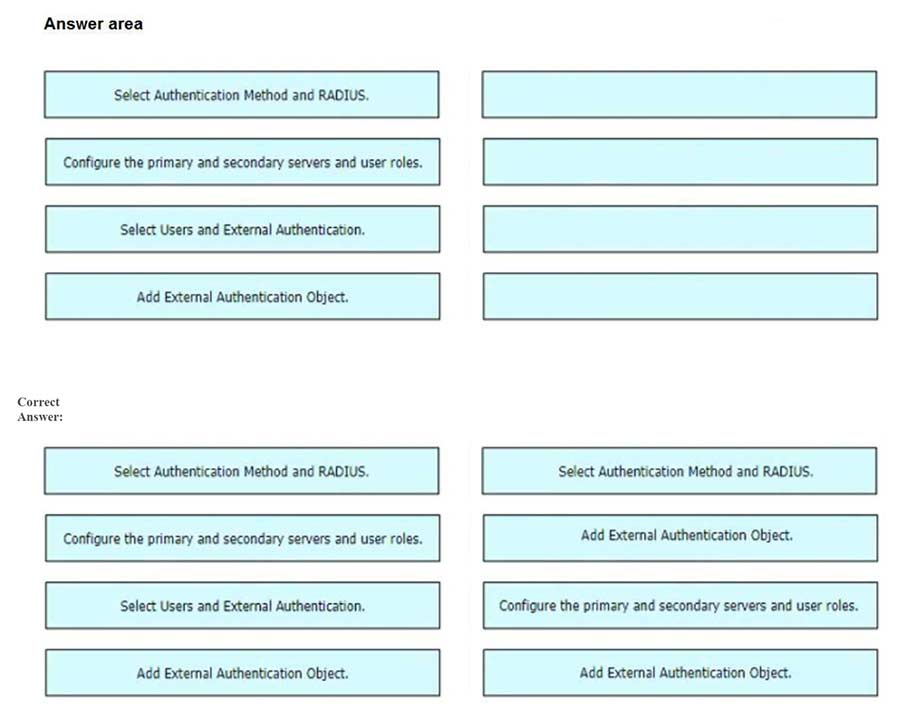
Drag and drop the configuration steps from the left into the sequence on the right to enable external authentication on Cisco FMC to a RADIUS server.
- A. Select Authentication Method and RADIUS.
- B. Configure the primary and secondary servers and user roles.
- C. Select Users and External Authentication.
- D. Add External Authentication Object.
Correct Answer:
Question 172
An engineer is creating an URL object on Cisco FMC. How must it be configured so that the object will match for HTTPS traffic in an access control policy?
- A. Specify the protocol to match (HTTP or HTTPS).
- B. Use the FQDN including the subdomain for the website.
- C. Use the subject common name from the website certificate.
- D. Define the path to the individual webpage that uses HTTPS.
Correct Answer: C
Question 173
Which action must be taken on the Cisco FMC when a packet bypass is configured in case the Snort engine is down or a packet takes too long to process?
- A. Enable Automatic Application Bypass.
- B. Add a Bypass Threshold policy for failures.
- C. Configure Fastpath rules to bypass inspection.
- D. Enable Inspect Local Router Traffic.
Correct Answer: A
Question 174
An engineer is configuring multiple Cisco FTD appliances for use in the network. Which rule must the engineer follow while defining interface objects in Cisco FMC for use with interfaces across multiple devices?
- A. Two security zones can contain the same interface.
- B. Interface groups can contain interfaces from many devices.
- C. An interface cannot belong to a security zone and an interface group.
- D. Interface groups can contain multiple interface types.
Correct Answer: B
Question 175
An administrator is adding a QoS policy to a Cisco FTD deployment. When a new rule is added to the policy and QoS is applied on “Interfaces in Destination Interface Objects”, no interface objects are available. What is the problem?
- A. The FTD is out of available resources for use, so QoS cannot be added.
- B. The network segments that the interfaces are on do not have contiguous IP space.
- C. A conflict exists between the destination interface types that is preventing QoS from being added.
- D. QoS is available only on routed interfaces, and this device is in transparent mode.
Correct Answer: D
Question 176
A network administrator wants to block traffic to a known malware site at https://www.badsite.com and all subdomains while ensuring no packets from any internal client are sent to that site. Which type of policy must the network administrator use to accomplish this goal?
- A. Access Control policy with URL filtering
- B. Prefilter policy
- C. DNS policy
- D. SSL policy
Correct Answer: C
Question 177
A network security engineer must export packet captures from the Cisco FMC web browser while troubleshooting an issue. When navigating to the address https:///capture/CAPY/pcap/test.pcap, an error 403: Forbidden is given instead of the PCAP file. Which action must the engineer take to resolve this issue?
- A. Disable the proxy setting on the browser
- B. Disable the HTTPS server and use HTTP instead
- C. Use the Cisco FTD IP address as the proxy server setting on the browser
- D. Enable the HTTPS server for the device platform policy
Correct Answer: D
Question 178
An analyst is investigating a potentially compromised endpoint within the network and pulls a host report for the endpoint in question to collect metrics and documentation. What information should be taken from this report for the investigation?
- A. Client applications by user, web applications, and user connections
- B. Number of attacked machines, sources of the attack, and traffic patterns
- C. Threat detections over time and application protocols transferring malware
- D. Intrusion events, host connections, and user sessions
Correct Answer: D
Question 179
An engineer must investigate a connectivity issue and decides to use the packet capture feature on Cisco FTD. The goal is to see the real packet going through the Cisco FTD device and see Snort detection actions as a part of the output. After the capture-traffic command is issued, only the packets are displayed. Which action resolves this issue?
- A. Specify the trace using the -T option after the capture-traffic command
- B. Perform the trace within the Cisco FMC GUI instead of the Cisco FMC CLI
- C. Use the verbose option as a part of the capture-traffic command
- D. Use the capture command and specify the trace option to get the required information
Correct Answer: D
Question 180
An analyst using the security analyst account permissions is trying to view the Correlations Events Widget but is not able to access it. However, other dashboards are accessible. Why is this occurring?
- A. The widget is configured to display only when active events are present.
- B. The security analyst role does not have permission to view this widget.
- C. An API restriction within the Cisco FMC is preventing the widget from displaying.
- D. The widget is not configured within the Cisco FMC.
Correct Answer: D
