
Pass 300-710 SNCF in Just 3 Days – Stress-Free!
Get your 300-710 Securing Networks with Cisco Firepower certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
Question 341
A security engineer sees an alert on Cisco Secure Endpoint console showing a malicious verdict for a file with the SHA-256 hash 0488537078abcdef048853abedef048853abedef048853abedef048853abedef048853. Which step will mitigate this threat?
- A. Add the hash to network block list.
- B. Quarantine the file on endpoint.
- C. Add the hash to custom detection list.
- D. Enable firewall on infected endpoint.
Correct Answer: C
Question 342
An engineer must configure and generate a report in Cisco Secure Firewall Management Center. The report must allow for the addition of headers and footers, and it will contain many pages. Which format must the engineer configure the report to use?
- A. PDF
- B. XLS
Correct Answer: A
Question 343
An engineer must investigate a connectivity issue by using Cisco Secure Firewall Management Center to access the Packet Capture feature on a Cisco Secure Firewall Threat Defense device. The engineer must see a real packet going through the Secure Firewall Threat Defense device and the Snort detection actions. While reviewing the packet capture, the engineer discovers that the Snort detection actions are missing. Which action must the engineer take to resolve the issue?
- A. Enable the Continuous Capture option.
- B. Enable the Trace option.
- C. Specify the packet size.
- D. Specify the buffer size.
Correct Answer: B
Question 344
An engineer is deploying failover capabilities for a pair of Cisco Secure Firewall devices. The core switch keeps the MAC address of the previously active unit in the ARP table. Which action must the engineer take to minimize downtime and ensure that network users keep access to the internet after a Cisco Secure Firewall failover?
- A. Use a virtual MAC address on both units.
- B. Add the MAC address to the switch ARP table.
- C. Set the same MAC address on both units.
- D. Run a script to send gratuitous ARP after a failover.
Correct Answer: D
Question 345
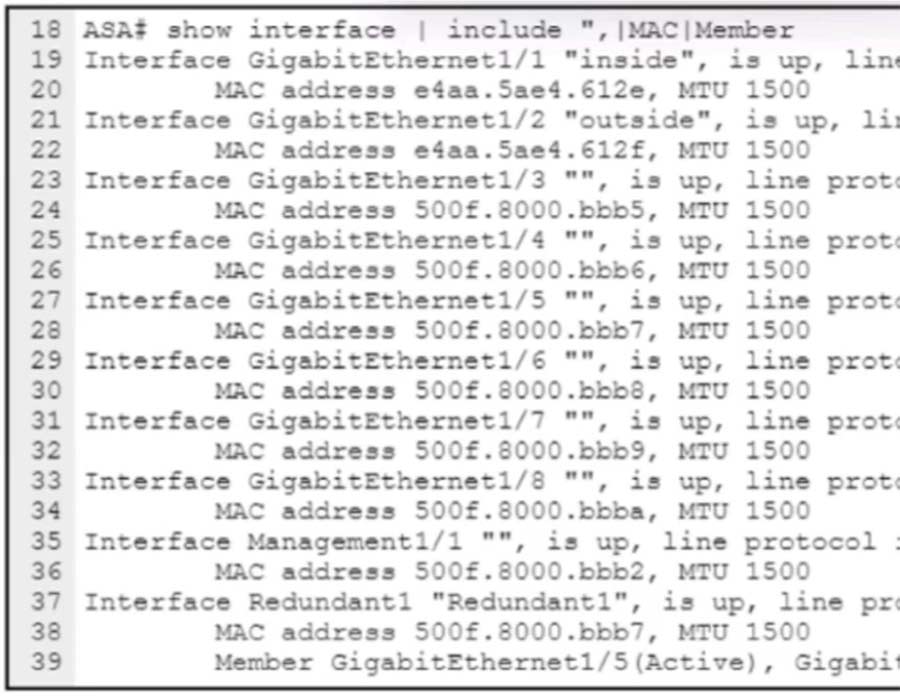
Refer to the exhibit. An engineer must configure a connection on a Cisco ASA 5500-X Series with a Cisco Secure Firewall Services Module to ensure that the secondary interface takes over all the functions of the primary interface if the primary interface fails. Drag and drop the code snippets from the bottom onto the boxes in the CLI commands to configure the failover. Not all options are used.
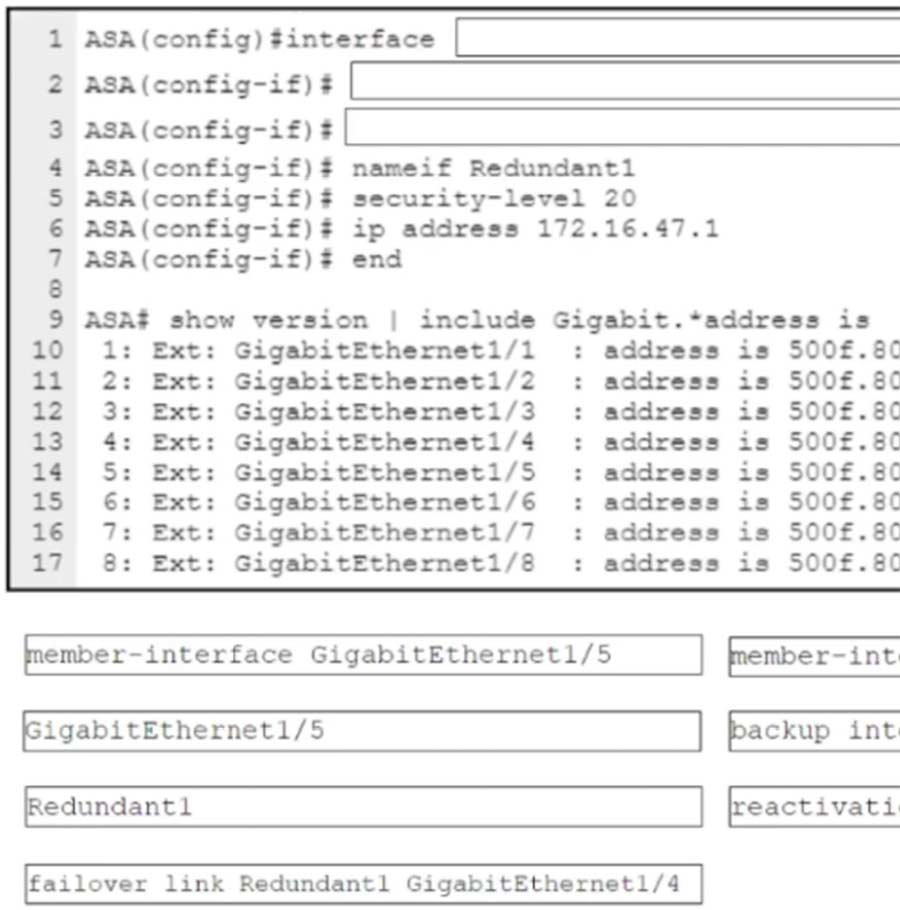
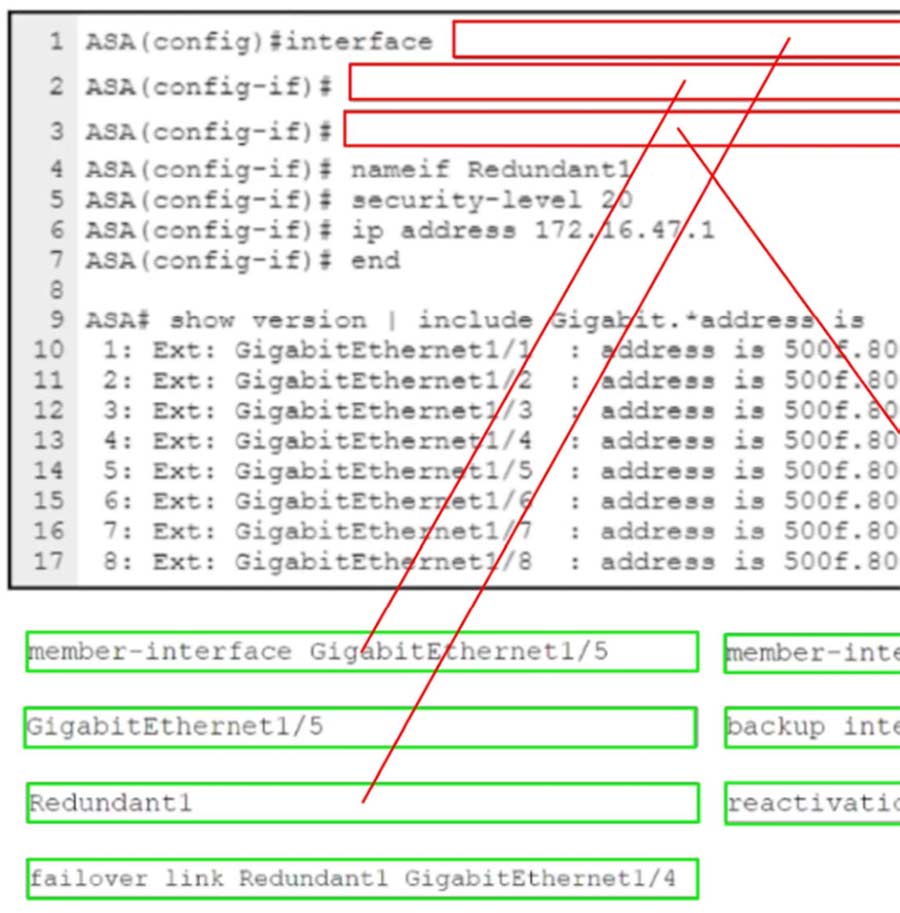
Correct Answer
Question 346
An engineer must deploy a Cisco Secure Firewall Threat Defense instance. The company wants the Secure Firewall Threat Defense deployment to allow business traffic in the event of any type of failure, and there must be no connectivity issues caused by the IPS in the perimeter of its data center. Which implementation mode must the engineer use?
- A. Hardware bypass
- B. Snort fail open
- C. Inline set
- D. Passive
Correct Answer: B
Question 347
Which firewall mode is Cisco Secure Firewall Threat Defense in when two physical interfaces are assigned to a named BVI?
- A. TPS only
- B. Routed
- C. Transparent
- D. Inline
Correct Answer: C
Question 348
A network administrator wants to configure a default policy to block malicious sites based on the requested URL lookup. Which feature meets the requirement?
- A. File policies
- B. Malware policies
- C. DNS policies
- D. URL filtering policies
Correct Answer: D
Question 349
An engineer must implement static route tracking on Cisco Secure Firewall Threat Defense and reroute traffic by using a backup path if the primary path fails. The engineer already defined the primary static route, and the primary path is already monitored. Which action must the engineer take to meet the requirement?
- A. Establish an IP SLA ICMP echo request.
- B. Configure a tracking object for the static route.
- C. Assign a unique tracking ID to the static route.
- D. Configure a secondary static route that has higher precedence.
Correct Answer: B
Question 350
A network engineer wants to disable the HTTP response page and interactive blocking of the entire access control policy in Cisco Secure Firewall Management Center. What must be selected in Block Response Page and Interactive Block Response Page?
- A. View
- B. Custom
- C. System
- D. None
Correct Answer: D
