
Pass 300-710 SNCF in Just 3 Days – Stress-Free!
Get your 300-710 Securing Networks with Cisco Firepower certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
Question 351
An engineer must reconfigure an NTP server on an IPSv device that is managed by using Cisco Secure Firewall Management Center. The engineer verified secure communications between Secure Firewall Management Center and the NTP server. How must the engineer perform the reconfiguration in Secure Firewall Management Center?
- A. Devices > Platform Settings > [assigned Secure Firewall Settings Policy] > Classic managed devices
- B. Devices > Device Management > [NGIPSv device] > Device > System
- C. Devices > Platform Settings > [assigned Threat Defense Settings Policy] > Time Synchronization
- D. Devices > Device Management > Time Synchronization
Correct Answer: C
Question 352
A network administrator is setting up a Cisco Secure Firewall Threat Defense to peer via BGP with two ISPs. The administrator wants traffic to certain IP ranges to prefer to come in one ISP instead of the other. What must be configured on the BGP connection to the peer to help facilitate the requirement?
- A. Prefix list
- B. Access list
- C. Address map
- D. Route map
Correct Answer: D
Question 353
A network administrator is configuring an instance of Cisco Secure Firewall Threat Defense, which is registered to Cisco Secure Firewall Management Center, to prevent internal users from downloading executable files from the internet. What must be created and configured by the administrator to meet the requirement?
- A. File policy that blocks downloads of all executable files and applies the file policy to the default action in the access policy
- B. Access policy rule that allows users to reach the internet with a second rule that blocks application executables
- C. File policy rule that allows users to reach the internet with a second rule applied that blocks application use of FTP
- D. Access policy rule that allows users to reach the internet and assigns a file policy that blocks executable downloads to the rule
Correct Answer: D
Question 354
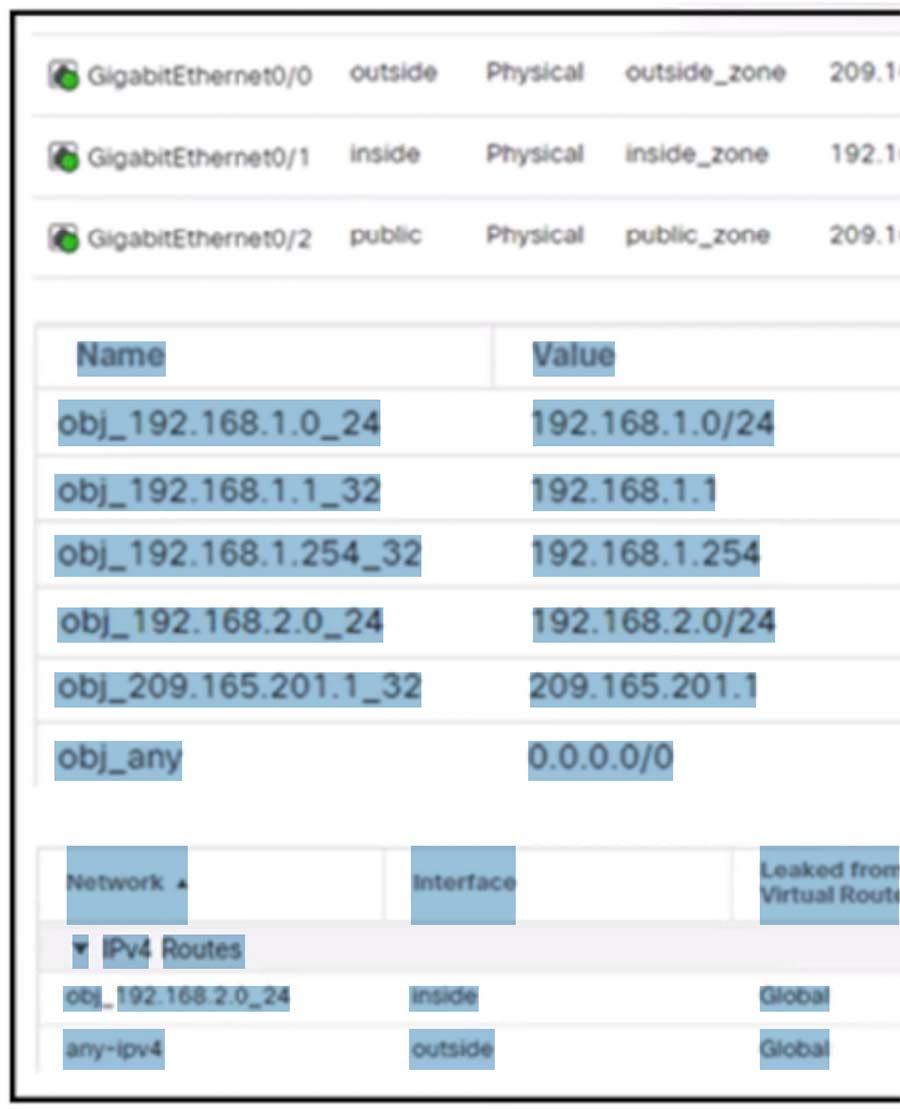
Refer to the exhibit. An engineer configures a NAT rule allowing clients to use the internet only if clients are located on the directly connected internal network. Dynamic auto PAT must be configured. Drag and drop the NAT rules from the left onto the corresponding targets on the right. Not all options are used.
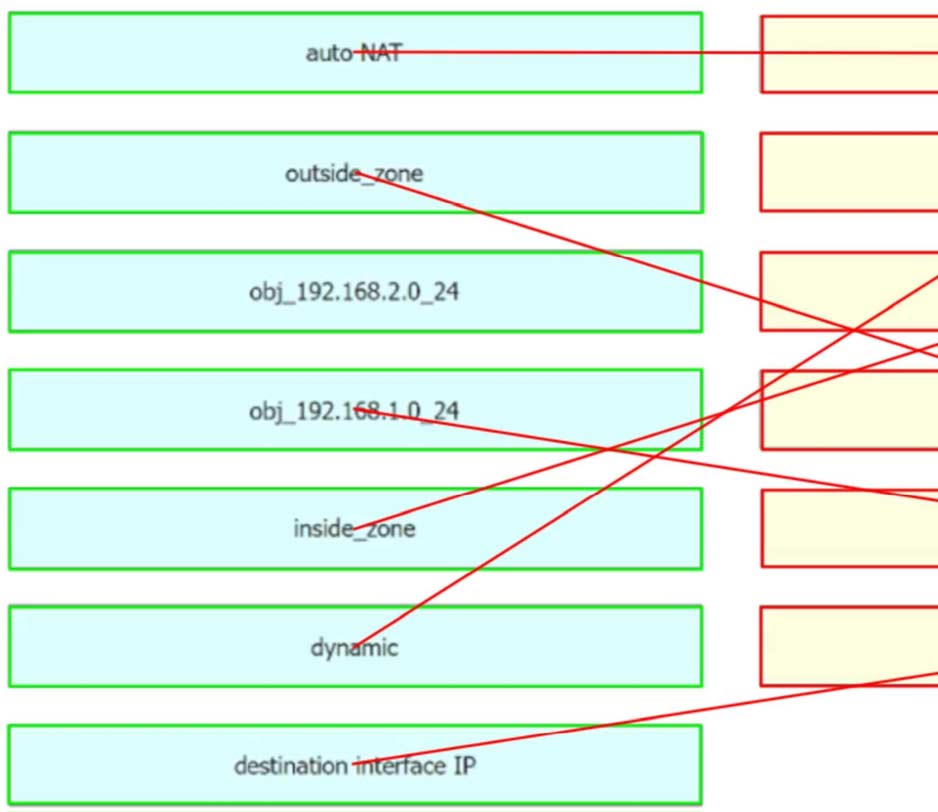
Correct Answer:
Question 355
An engineer must export a packet capture from Cisco Secure Firewall Management Center to assist in troubleshooting an issue on a Secure Firewall Threat Defense device. When the engineer navigates to the URL for Secure Firewall Management Center at: https:///capture/CAPY/pcap/sample.pcap. The engineer receives a 403: Forbidden error instead of being provided with the PCAP file. Which action resolves the issue?
- A. Disable the proxy setting on the client browser.
- B. Disable the HTTPS server and use HTTP.
- C. Enable HTTPS in the device platform policy.
- D. Enable the proxy setting in the device platform policy.
Correct Answer: D
Question 356
Which Cisco Secure Firewall Management Center widget is authorized only for users with administrator access?
- A. Product licensing
- B. Appliance information
- C. System load
- D. Current sessions
Correct Answer: D
Question 357
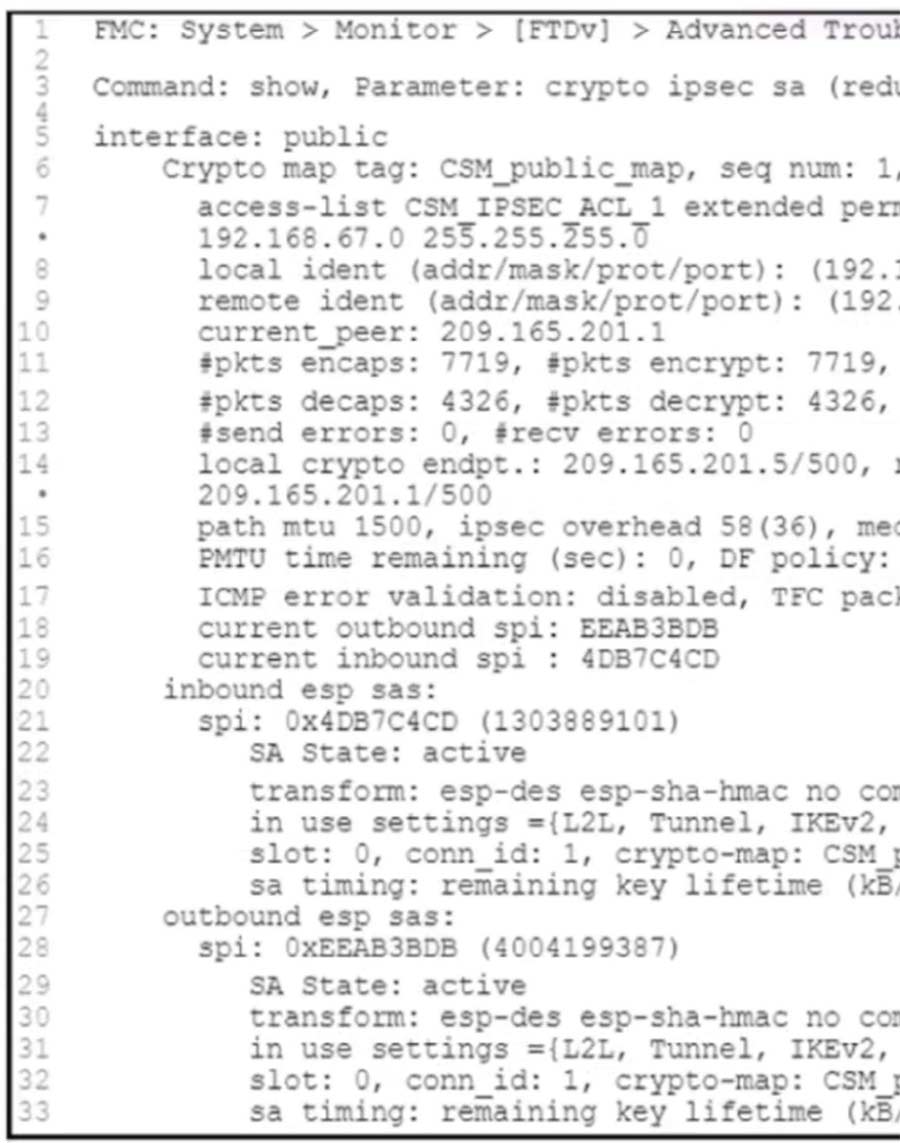
Refer to the exhibit. An engineer is troubleshooting connectivity issues over a VPN tunnel. Users from the 192.168.68.0/24 network report that they cannot connect to a remote web server that has an IP address of 192.168.67.100. The engineer confirms that NAT and access control rules on the local Cisco Secure Firewall Threat Defense Virtual will allow the connection. Which two configuration changes must the engineer make to resolve the connectivity issues?
- A. Unblock the remote firewall connection.
- B. Set the VPN to support two-way traffic.
- C. Bring the VPN tunnel up.
- D. Match the crypto access control list.
- E. Reconfigure the web server.
Correct Answer: C, D
Question 358
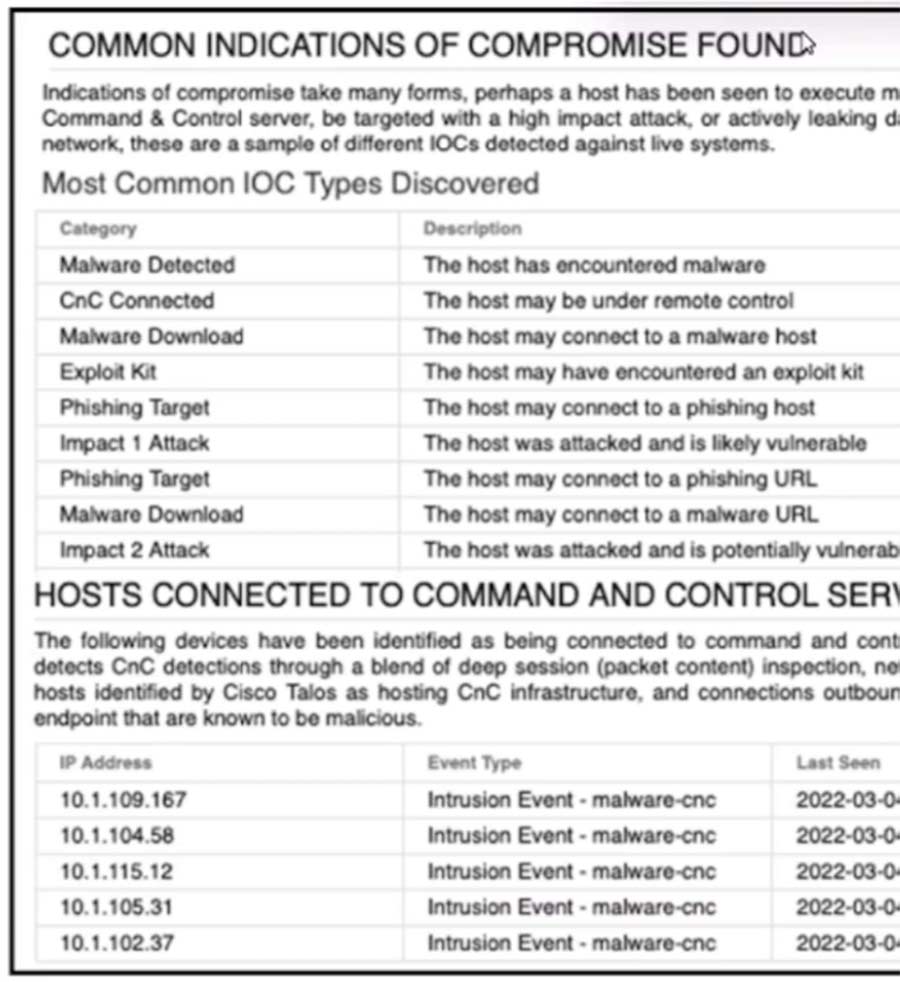
Refer to the exhibit. An engineer analyzes a Network Risk Report from Cisco Secure Firewall Management Center. What should the engineer recommend implementing to mitigate the risk?
- A. Trend analysis
- B. Network-based detection
- C. Virtual protection
- D. IP address and URL blacklisting
Correct Answer: D
Question 359
A security engineer is reviewing a Cisco Secure Endpoint public cloud instance. The engineer discovers a malicious verdict for a SHA-256 hash of 689efclecdc23ec0b0885a80663e30ea013d493f8e88224b570a1234567890. Which configuration action must be done in Secure Endpoint console to mitigate the threat?
- A. Add the hash to the custom detection list.
- B. Set access control policy and deny files with the hash.
- C. Configure correlation policy to block the hash.
- D. Apply regular expression to block the malicious file.
Correct Answer: A
Question 360
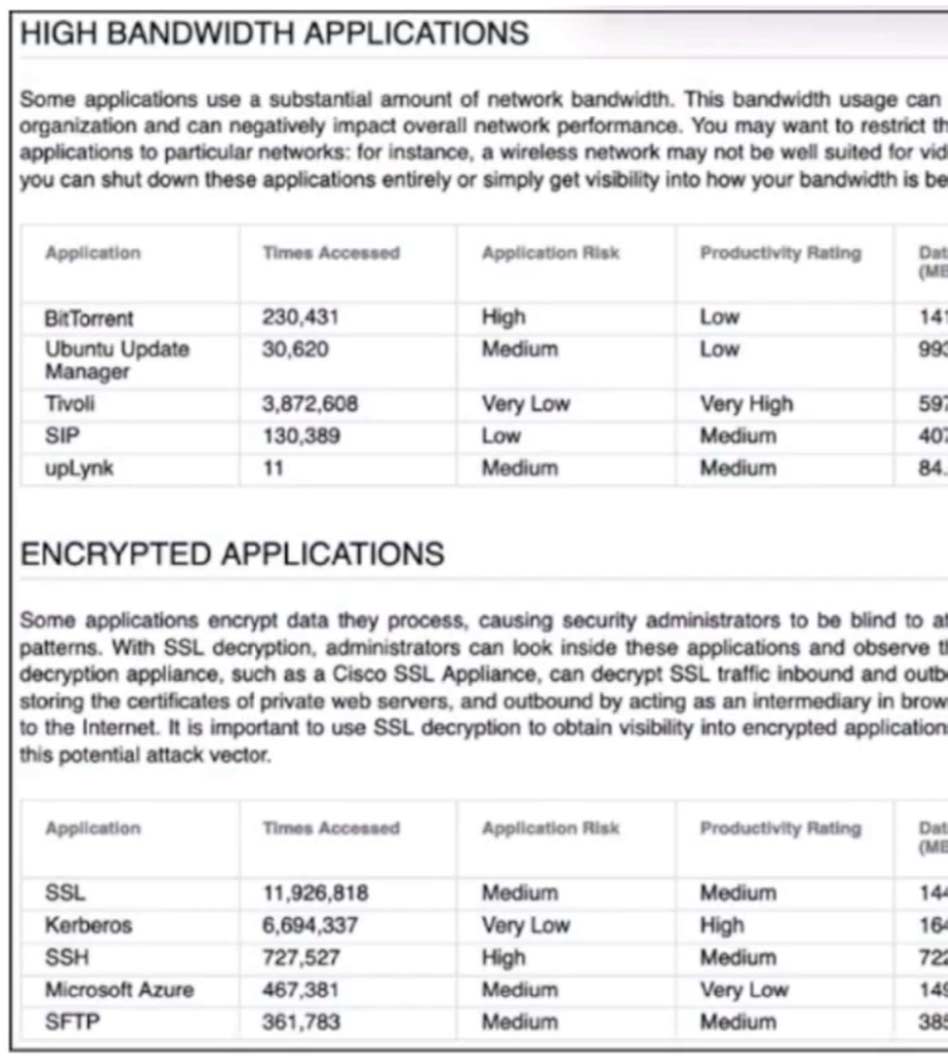
Refer to the exhibit. A network engineer is analyzing a Network Risk Report generated in Cisco Secure Firewall Management Center that focuses on network security and efficient bandwidth utilization. Which application should be restricted?
- A. BitTorrent
- B. SFTP
- C. Tivoli
- D. SSH
Correct Answer: B
