
Pass 300-710 SNCF in Just 3 Days – Stress-Free!
Get your 300-710 Securing Networks with Cisco Firepower certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
Question 371
An engineer must configure email notifications on Cisco Secure Firewall Management Center. TLS encryption must be used to protect the messages from unauthorized access. The engineer adds the IP address of the mail relay host and must set the port number. Which TCP port must the engineer use?
- A. 25
- B. 389
- C. 465
- D. 587
Correct Answer: D
Question 372
After a network security breach, an engineer must strengthen the security of the corporate network. Upper management must be regularly updated with a high-level overview of any occurring network threats. Which access must the engineer provide upper management to view the required data from Cisco Secure Firewall Management Center?
- A. Analysis > Status with a sliding time window of one day.
- B. Events by priority and classification and set a sliding time window of one day.
- C. Security Intelligence Statistics dashboard set to Show the Last option.
- D. Reports with a daily recurring task that generates based on the network risk report template.
Correct Answer: D
Question 373
An engineer must permit SSH on the inside interface of a Cisco Secure Firewall Threat Defense device. SSH is currently permitted only on the management interface. Which type of policy must the engineer configure?
- A. platform policy.
- B. intrusion policy.
- C. NAT policy.
- D. access control policy.
Correct Answer: D
Question 374
Which feature sets up multiple interfaces on a Cisco Secure Firewall Threat Defense to be on the same subnet?
- A. EtherChannel
- B. svi
- C. BVI
- D. security levels
Correct Answer: C
Question 375
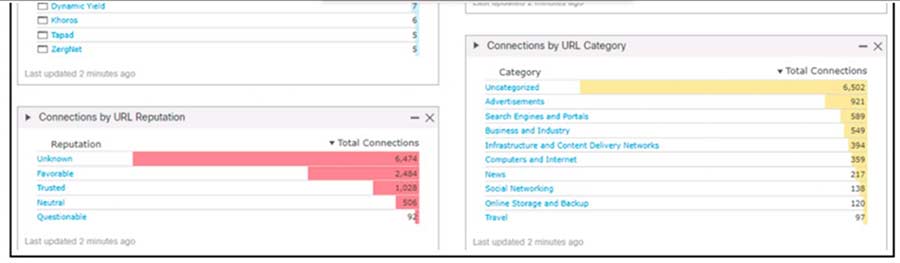
Refer to the exhibit. An engineer analyzes a Cisco Firepower Management Center dashboard. Which action must be taken by the user to decrease the risk of data loss?
- A. Stop all the URLs that are uncategorized.
- B. Block the use of Dropbox.
- C. Stop all URLs that have an unknown reputation.
- D. Block all the BitTorrent applications.
Correct Answer: C
Question 376
An engineer is deploying Cisco Secure Endpoint for the first time and on endpoint with MAC address 50:48:70:28:0:AB. The engineer must make sure that
during the testing phase no files are isolated and network connections must not be blocked. Which policy type must be configured to accomplish the task?
- A. Protect
- B. Triage
- C. Audit
- D. Quarantine
Correct Answer: C
Question 377
An engineer must perform a packet capture on a Cisco Secure Firewall Threat Defense device to confirm the MAC address of the host using IP address 192.168.100.100 while troubleshooting an ARP issue. What is the correct tepdump command syntax to ensure that the MAC address appears in the packet capture output?
- A. -nm src 192.168.100.100
- B. -w capture.pcap -5 1518 host 192.168.100.100 ether
- C. -w capture.pcap -5 1518 host 192.168.100.100 mac
- D. -ne src 192.168.100.100
Correct Answer: D
Question 377
An engineer is troubleshooting the upgrade of a Cisco Secure Firewall Threat Defense device on the Secure Firewall Management Center 7.0 GUI. The engineer wants to collect the upgrade data and logs. Which two actions must the engineer take? (Choose two.)
- A. Access the Health Monitor page.
- B. Select the Secure Firewall Threat Defense device properties.
- C. Access the Health Events page.
- D. Select the Secure Firewall Management Center device.
- E. ew the system and troubleshooting details.
Correct Answer: B, E
Question 378
A network engineer must monitor threat events from the console of Cisco Secure Firewall Management Center. The engineer integrates the Cisco Secure Firewall Malware Defense in Secure Firewall Management Center. Which action must the engineer take next?
- A. Login to Secure Endpoint, click Allow to authorize the Secure Firewall Malware Defense to Secure FMC connection, add a Secure Firewall Malware Defense cloud connection to Secure FMC, and select the Secure Firewall Malware Defense cloud for Secure Endpoint.
- B. Add a Secure Firewall Malware Defense cioud connection in Secure FMC, log in to Secure Endpoint, and click Allow to authorize the Secure Firewall Malware Defense to Secure FMC connection.
- C. Add a Securs Firewall Malware Defense cloud connection in Secure FMC, select the Secure Firewall Malware Defense cloud for Secure Endpoint, log in to Securs Endpoint, and click Allow to
authorize the Secure Firewall Malware Defense to Secure FMC connection. - D. Log In to Cisco Secure Endpoint, click Allow to authorize the Secure Firewall Malware Defense to Secure FMC connection, and add a Secure Firewall Malware Defense cloud connection to Secure FMC.
Correct Answer: B
Question 379
An engineer must configure a correlation policy in Cisco Secure Firewall Management Genter to detect when an IP address from an internal network communicates with a known malicious host. Connections made by the internal IP addresses must be tracked, and an extemal dynamic list must be used for the condition. Which type of event must the engineer configure on the correlation policy?
- A. malware
- B. network discovery
- C. Intrusion Impact Alert
- D. connection tracker
Correct Answer: D
Question 380
Users report that Gisco Duo 2FA fails when they attempt to connect fo the VPN on a Cisco Secure Firewall Threat Defense device. IT staff have VPN profiles that do not require multifactor authentication and they can connect to the VPN without any issues. When viewing the VPN troubleshooting log in Cisco Secure Firewall Management Center, the network administrator sees an error that the Cisco Duo AAA
server has been marked as failed. What is the root cause of the issue?
- A. malware
- B. network discovery
- C. Intrusion Impact Alert
- D. connection tracker
Correct Answer: D
