
Pass 300-710 SNCF in Just 3 Days – Stress-Free!
Get your 300-710 Securing Networks with Cisco Firepower certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
Question 61
An administrator is working on a migration from Cisco ASA to the Cisco FTD appliance and needs to test the rules without disrupting the traffic. Which policy type should be used to configure the ASA rules during this phase of the migration?
- A. Prefilter
- B. Intrusion
- C. Access Control
- D. Identity
Correct Answer: C
Question 62
A network administrator is seeing an unknown verdict for a file detected by Cisco FTD. Which malware policy configuration option must be selected in order to further analyze the file in the Talos cloud?
- A. Malware analysis
- B. Dynamic analysis
- C. Sandbox analysis
- D. Spero analysis
Correct Answer: B
Question 63
An engineer has been tasked with providing disaster recovery for an organization’s primary Cisco FMC. What must be done on the primary and secondary Cisco FMCs to ensure that a copy of the original corporate policy is available if the primary Cisco FMC fails?
- A. Restore the primary Cisco FMC backup configuration to the secondary Cisco FMC device when the primary device fails.
- B. Connect the primary and secondary Cisco FMC devices with Category 6 cables of not more than 10 meters in length.
- C. Configure high-availability in both the primary and secondary Cisco FMCs.
- D. Place the active Cisco FMC device on the same trusted management network as the standby device.
Correct Answer: C
Question 64
An engineer is attempting to add a new FTD device to their FMC behind a NAT device with a NAT ID of ACMEO0! and a password of Cisco0391521107. Which command set must be used in order to accomplish this?
- A. configure manager add ACMEO001
- B. configure manager add ACMEOQ01
- C. configure manager add ACMEO01
- D. configure manager add DONTRESOLVE ACMEO001
Correct Answer: D
Question 65
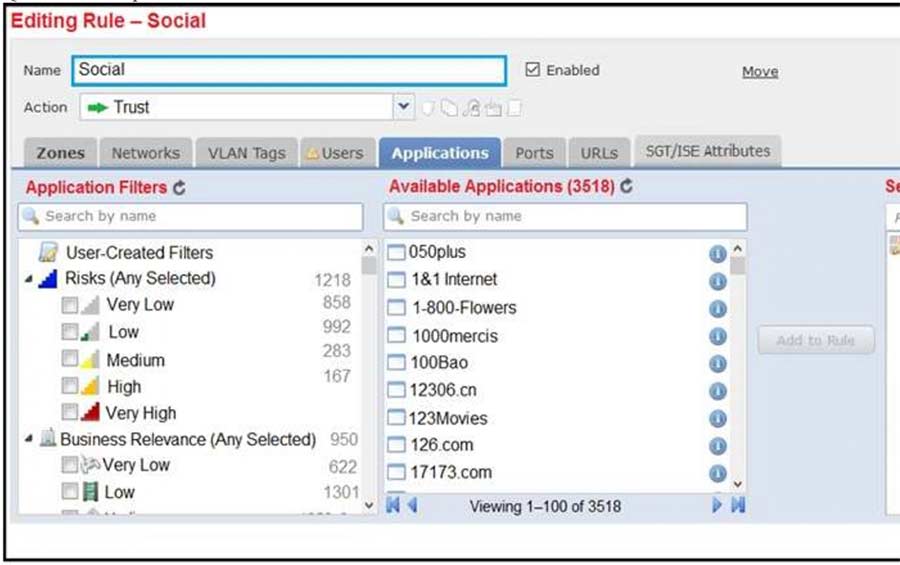
Refer to the exhibit. An organization has an access control rule with the intention of sending all social media traffic for inspection. After using the rule for some time, the administrator notices that the traffic is not being inspected, but is being automatically allowed. What must be done to address this issue?
- A. Add the social network URLs to the block list.
- B. Change the intrusion policy to connectivity over security.
- C. Modify the selected application within the rule.
- D. Modify the rule action from trust to allow.
Correct Answer: D
Question 66
A user within an organization opened a malicious file on a workstation which in turn caused a ransomware attack on the network. What should be configured within the Cisco FMC to ensure the file is tested for viruses on a sandbox system?
- A. Spero analysis
- B. Capacity handling
- C. Local malware analysis
- D. Dynamic analysis
Correct Answer: D
Question 67
An engineer configures a network discovery policy on Cisco FMC. Upon configuration, it is noticed that excessive and misleading events are filling the database and overloading the Cisco FMC. A monitored NAT device is executing multiple updates of its operating system in a short period of time. What configuration change must be made to alleviate this issue?
- A. Exclude load balancers and NAT devices.
- B. Leave default networks.
- C. Increase the number of entries on the NAT device.
- D. Change the method to TCP/SYN.
Correct Answer: A
Question 68
A network administrator notices that remote access VPN users are not reachable from inside the network. It is determined that routing is configured correctly; however, return traffic is entering the firewall but not leaving it. What is the reason for this issue?
- A. A manual NAT exemption rule does not exist at the top of the NAT table.
- B. An external NAT IP address is not configured.
- C. An external NAT IP address is configured to match the wrong interface.
- D. An object NAT exemption rule does not exist at the top of the NAT table.
Correct Answer: A
Question 69
An administrator is creating interface objects to better segment their network but is having trouble adding interfaces to the objects. What is the reason for this failure?
- A. The interfaces are being used for NAT for multiple networks.
- B. The administrator is adding interfaces of multiple types.
- C. The administrator is adding an interface that is in multiple zones.
- D. The interfaces belong to multiple interface groups.
Correct Answer: B
Question 70
An organization is using a Cisco FTD and Cisco ISE to perform identity-based access controls. A network administrator is analyzing the Cisco FTD events and notices that unknown user traffic is being allowed through the firewall. How should this be addressed to block the traffic while allowing legitimate user traffic?
- A. Modify the Cisco ISE authorization policy to deny this access to the user.
- B. Modify Cisco ISE to send only legitimate usernames to the Cisco FTD.
- C. Add the unknown user in the Access Control Policy in Cisco FTD.
- D. Add the unknown user in the Malware & File Policy in Cisco FTD.
Correct Answer: C
