We HELP you PASS (CCNP 350-401) Implementing Cisco Enterprise Network Core Technologies (ENCOR) certification, without exam and training!
***Pay after you Pass***
What is a benefit of using a Type 2 hypervisor instead of a Type 1 hypervisor?
- A. better application performance
- B. improved security because the underlying OS is eliminated
- C. improved density and scalability
- D. ability to operate on hardware that is running other OSs
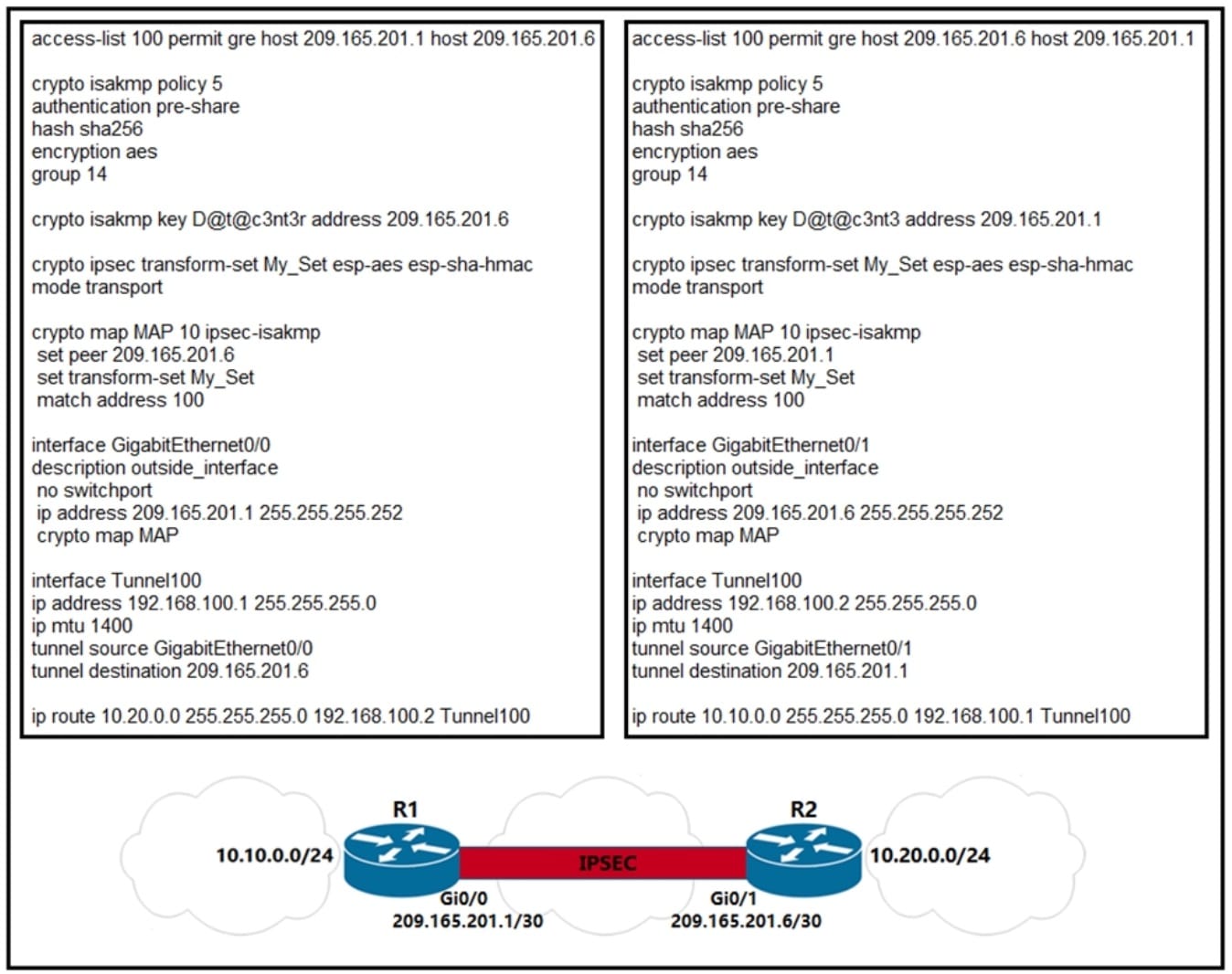
Refer to the exhibit. A network engineer must simplify the IPsec configuration by enabling IPsec over GRE using IPsec profiles. Which two configuration changes accomplish this? (Choose two).
- A. Create an IPsec profile, associate the transform-set ACL, and apply the profile to the tunnel interface.
- B. Apply the crypto map to the tunnel interface and change the tunnel mode to tunnel mode ipsec ipv4.
- C. Remove all configuration related to crypto map from R1 and R2 and eliminate the ACL.
- D. Create an IPsec profile, associate the transform-set, and apply the profile to the tunnel interface.
- E. Remove the crypto map and modify the ACL to allow traffic between 10.10.0.0/24 to 10.20.0.0/24.
What is a benefit of a virtual machine when compared with a physical server?
- A. Multiple virtual servers can be deployed on the same physical server without having to buy additional hardware.
- B. Virtual machines increase server processing performance.
- C. The CPU and RAM resources on a virtual machine cannot be affected by other virtual machines.
- D. Deploying a virtual machine is technically less complex than deploying a physical server.
What is required for a virtual machine to run?
- A. a Type 1 hypervisor and a host operating system
- B. a hypervisor and physical server hardware
- C. only a Type 1 hypervisor
- D. only a Type 2 hypervisor
What are two benefits of virtual switching when compared to hardware switching? (Choose two.)
- A. increased MTU size
- B. VM-level isolation
- C. extended 802.1Q VLAN range
- D. hardware independence
- E. increased flexibility
What is a characteristic of a virtual machine?
- A. It must run the same operating system as its host.
- B. It is deployable without a hypervisor to host it.
- C. It must be aware of other virtual machines, in order to allocate physical resources for them.
- D. It relies on hypervisors to allocate computing resources for it.
Which LISP component is required for a LISP site to communicate with a non-LISP site?
- A. Proxy ITR
- B. ITR
- C. ETR
- D. Proxy ETR
Which two components are supported by LISP? (Choose two.)
- A. proxy ETR
- B. egress tunnel router
- C. route reflector
- D. HMAC algorithm
- E. spoke
What is the function of a VTEP in VXLAN?
- A. provide the routing underlay and overlay for VXLAN headers
- B. dynamically discover the location of end hosts in a VXLAN fabric
- C. encapsulate and de-encapsulate traffic into and out of the VXLAN fabric
- D. statically point to end host locations of the VXLAN fabric
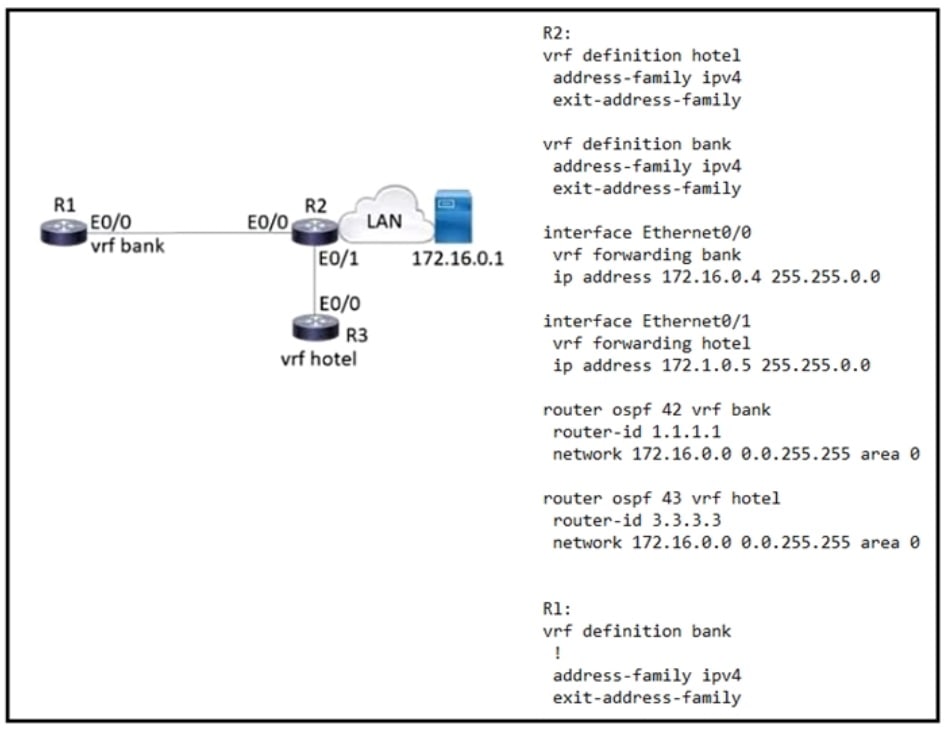
Refer to the exhibit. Which configuration must be applied to R1 to enable R1 to reach the server at 172.16.0.1?
- A. interface Ethernet0/0 ip address 172.16.0.7 255.255.0.0 router ospf 44 vrf bank network 172.16.0.0 255.255.0.0
- B. interface Ethernet0/0 vrf forwarding hotel ip address 172.16.0.7 255.255.0.0 router ospf 44 vrf Hotel network 172.16.0.0 0.0.255.255 area 0
- C. interface Ethernet0/0 vrf forwarding bank ip address 172.16.0.7 255.255.0.0 router ospf 44 vrf bank network 172.16.0.0 0.0.255.255 area 0
- D. interface Ethernet0/0 ip address 172.16.0.7 255.255.0.0 router ospf 44 vrf hotel network 172.16.0.0 255.255.0.0
