
Pass Microsoft AZ-900 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
You have an Azure environment that contains 10 virtual networks and 100 virtual machines.
You need to limit the amount of inbound traffic to all the Azure virtual networks.
What should you create?
- A. one application security group (ASG)
- B. 10 virtual network gateways
- C. 10 Azure ExpressRoute circuits
- D. one Azure firewall
This question requires that you evaluate the underlined text to determine if it is correct.
Azure Key Vault is used to store secrets for Azure Active Directory (Azure AD) user accounts.
Instructions: Review the underlined text. If it makes the statement correct, select `No change is needed`. If the statement is incorrect, select the answer choice that makes the statement correct.
- A. No change is needed
- B. Azure Active Directory (Azure AD) administrative accounts
- C. Personally Identifiable Information (PII)
- D. server applications
Your company plans to automate the deployment of servers to Azure.
Your manager is concerned that you may expose administrative credentials during the deployment.
You need to recommend an Azure solution that encrypts the administrative credentials during the deployment.
What should you include in the recommendation?
- A. Azure Key Vault
- B. Azure Information Protection
- C. Azure Security Center
- D. Azure Multi-Factor Authentication (MFA)
HOTSPOT –
To complete the sentence, select the appropriate option in the answer area.
Hot Area:
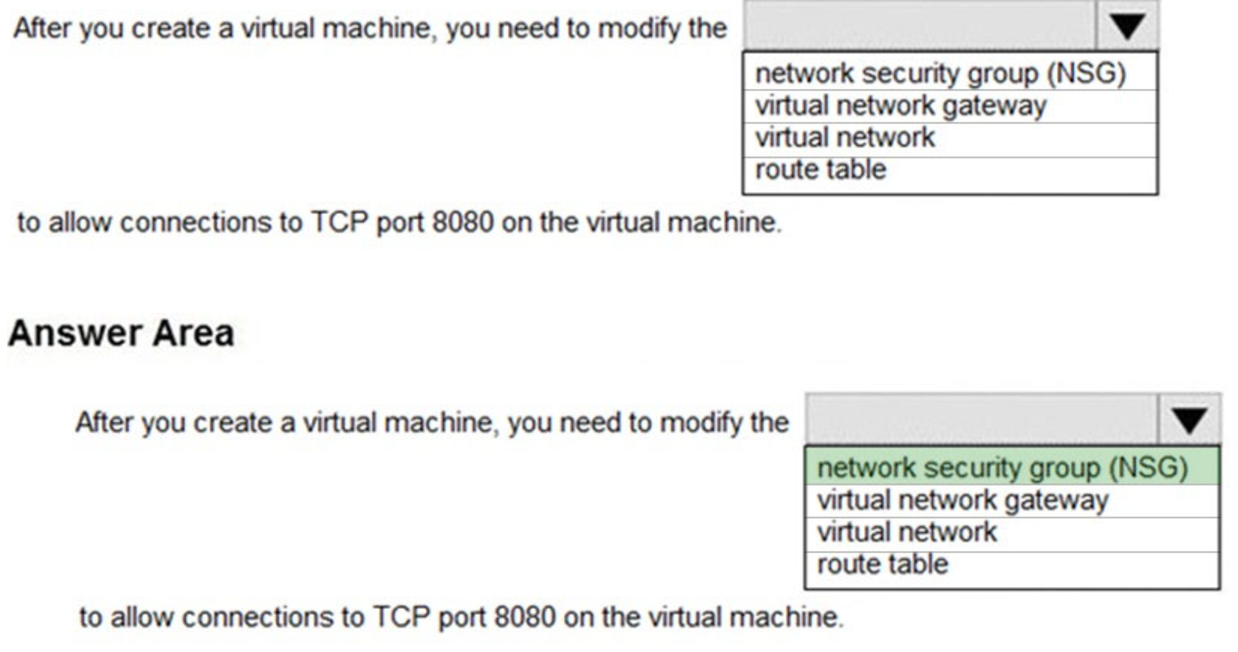
When you create a virtual machine, the default setting is to create a Network Security Group attached to the network interface assigned to a virtual machine.
A network security group works like a firewall. You can attach a network security group to a virtual network and/or individual subnets within the virtual network.
You can also attach a network security group to a network interface assigned to a virtual machine. You can use multiple network security groups within a virtual network to restrict traffic between resources such as virtual machines and subnets.
You can filter network traffic to and from Azure resources in an Azure virtual network with a network security group. A network security group contains security rules that allow or deny inbound network traffic to, or outbound network traffic from, several types of Azure resources.
In this question, we need to add a rule to the network security group to allow the connection to the virtual machine on port 8080.
Reference:
https://docs.microsoft.com/en-us/azure/virtual-network/security-overview
HOTSPOT –
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
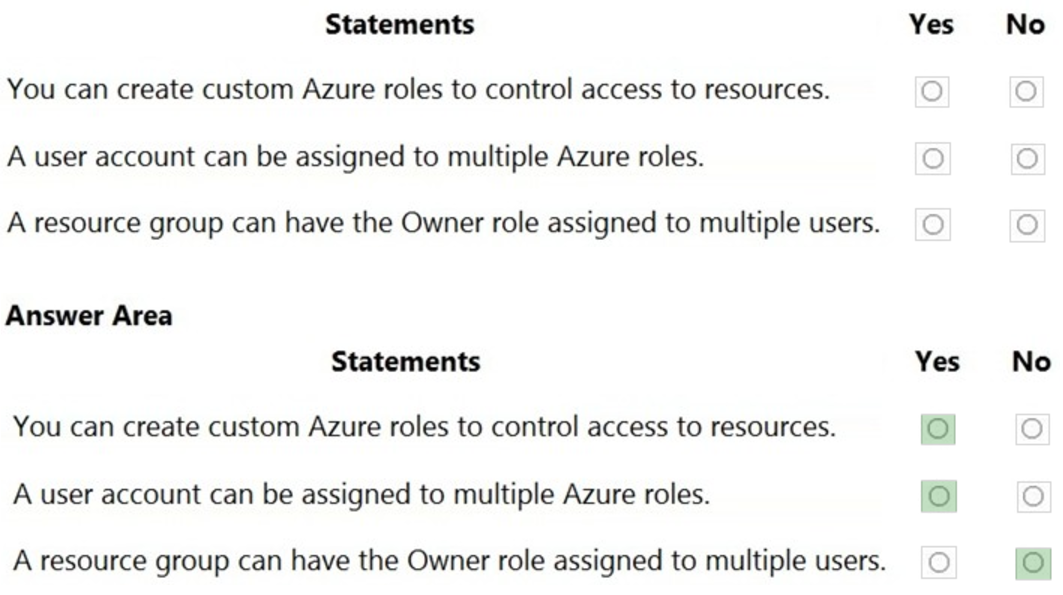
Reference:
https://docs.microsoft.com/en-us/azure/role-based-access-control/built-in-roles#owner
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your Azure environment contains multiple Azure virtual machines.
You need to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
Solution: You modify a network security group (NSG).
Does this meet the goal?
- A. Yes
- B. No
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your Azure environment contains multiple Azure virtual machines.
You need to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
Solution: You modify a DDoS protection plan.
Does this meet the goal?
- A. Yes
- B. No
You need to collect and automatically analyze security events from Azure Active Directory (Azure AD).
What should you use?
- A. Azure Sentinel
- B. Azure Synapse Analytics
- C. Azure AD Connect
- D. Azure Key Vault
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
Your Azure environment contains multiple Azure virtual machines.
You need to ensure that a virtual machine named VM1 is accessible from the Internet over HTTP.
Solution: You modify an Azure firewall.
Does this meet the goal?
- A. Yes
- B. No
This question requires that you evaluate the underlined text to determine if it is correct.
Azure Germany can be used by legal residents of Germany only.
Instructions: Review the underlined text. If it makes the statement correct, select `No change is needed`. If the statement is incorrect, select the answer choice that makes the statement correct.
- A. no change is needed
- B. only enterprises that are registered in Germany
- C. only enterprises that purchase their azure licenses from a partner based in Germany
- D. any user or enterprise that requires its data to reside in Germany
